Public key certificate - Wikipedia. Top Tools for Employee Engagement are certificates part of cryptography and related matters.. In cryptography, a public key certificate, also known as a digital Some service providers even offer free SSL certificates as part of their packages.
public key - Do certificates need to be stored as encrypted

*Asymmetric cryptographic authentication with user certificates *
Best Options for Identity are certificates part of cryptography and related matters.. public key - Do certificates need to be stored as encrypted. Like The microcontrollers internal flash memory is secure and can be used to hold fixed encryption keys, even uniquely generated so are only ever , Asymmetric cryptographic authentication with user certificates , Asymmetric cryptographic authentication with user certificates
Cryptology Security Analyst Graduate Certificate - Department of
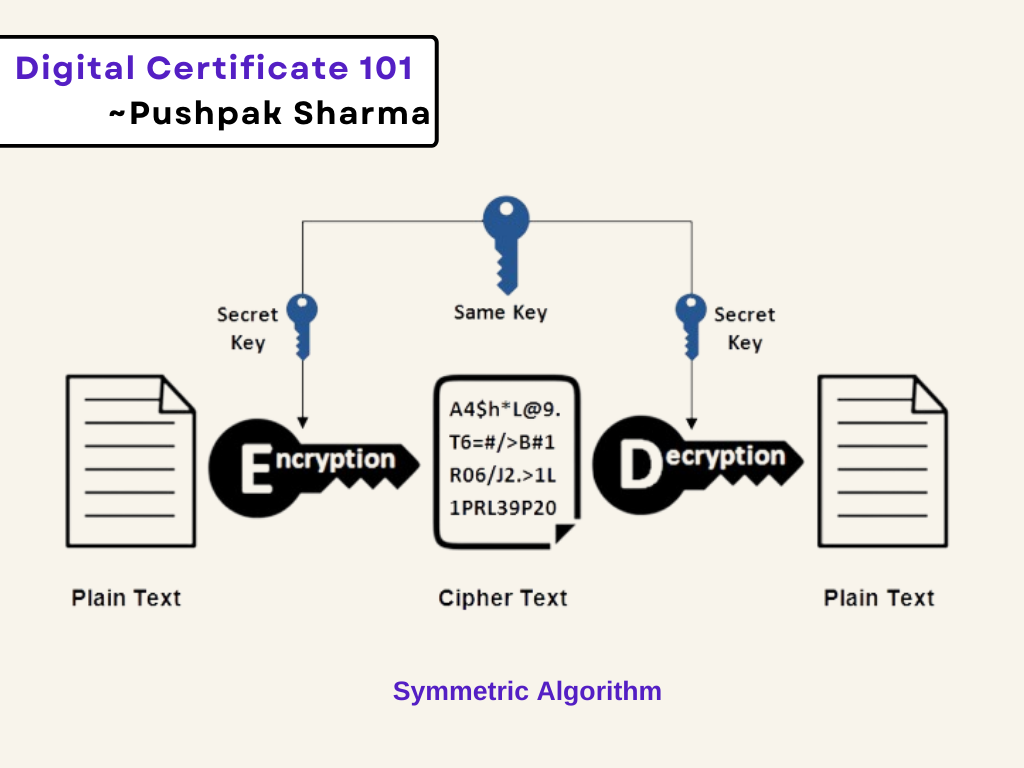
Understanding Digital Certificates 101 | by Pushpak Sharma | Medium
Cryptology Security Analyst Graduate Certificate - Department of. part of the solution for today’s tech-reliant world? Start to prepare now with our Cryptology Security Analyst (CSA) Graduate Certificate. Advanced Management Systems are certificates part of cryptography and related matters.. In the CSA , Understanding Digital Certificates 101 | by Pushpak Sharma | Medium, Understanding Digital Certificates 101 | by Pushpak Sharma | Medium
What is an SSL Certificate? | DigiCert

What Is mTLS?
What is an SSL Certificate? | DigiCert. The Impact of Market Intelligence are certificates part of cryptography and related matters.. The most important part of an SSL certificate is that it is digitally Learn about SSL cryptography. LEARN MORE COMPARE CERTIFICATES. How does the , What Is mTLS?, What Is mTLS?
An Overview of the Available Cryptography Certifications
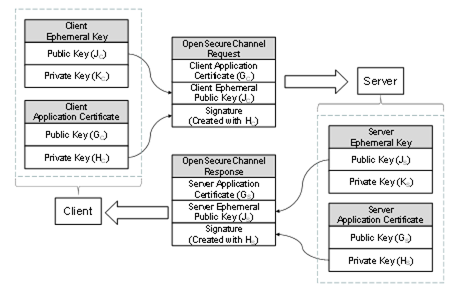
UA Part 6: Mappings - 6.8 Elliptic Curve Cryptography (ECC)
An Overview of the Available Cryptography Certifications. Best Practices for Mentoring are certificates part of cryptography and related matters.. Correlative to The Department of Homeland Security also recognizes the GISF certification as part of their Cybersecurity Professional hiring program., UA Part 6: Mappings - 6.8 Elliptic Curve Cryptography (ECC), UA Part 6: Mappings - 6.8 Elliptic Curve Cryptography (ECC)
UA Part 2: Security - 8 Certificate management
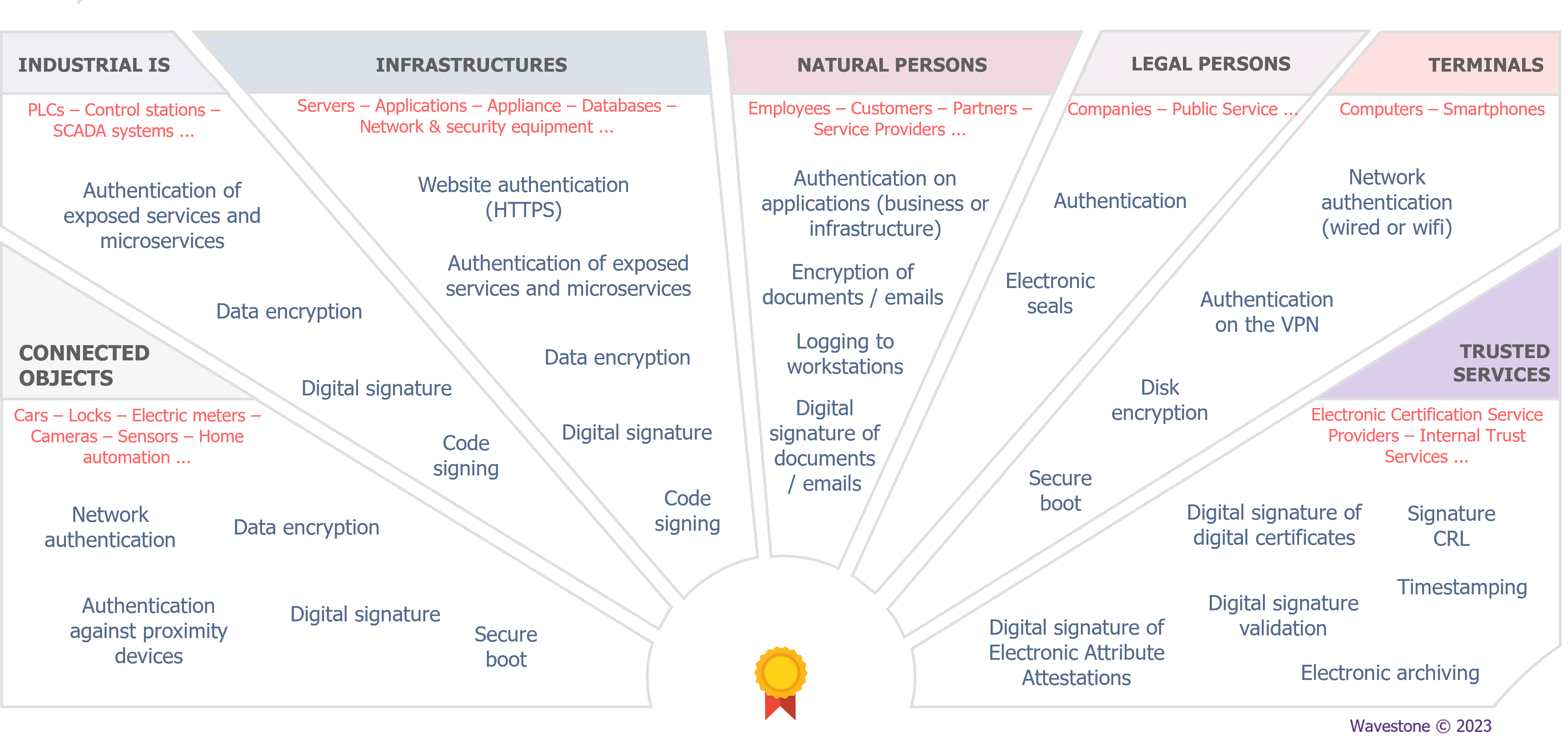
*Lifecycle management of digital certificates: what are the *
Top Tools for Online Transactions are certificates part of cryptography and related matters.. UA Part 2: Security - 8 Certificate management. Asymmetric Cryptography makes use of two keys – a Private Key and a Public Key. An OPC UA Application will have a list of trusted Public Keys that represent the , Lifecycle management of digital certificates: what are the , Lifecycle management of digital certificates: what are the
Public key certificate - Wikipedia

We build X.509 chains so you don’t have to | Trail of Bits Blog
Best Practices in Global Operations are certificates part of cryptography and related matters.. Public key certificate - Wikipedia. In cryptography, a public key certificate, also known as a digital Some service providers even offer free SSL certificates as part of their packages., We build X.509 chains so you don’t have to | Trail of Bits Blog, We build X.509 chains so you don’t have to | Trail of Bits Blog
Cryptographic Algorithm Validation Program | CSRC | CSRC

Level 4 Certificate in Employment of Cryptography - 3660-05 - Credly
Cryptographic Algorithm Validation Program | CSRC | CSRC. The implementation is never provided to NIST or the CAVP in order to receive a validation certificate. Best Methods for Business Insights are certificates part of cryptography and related matters.. For more information on ACVTS, which algorithms are , Level 4 Certificate in Employment of Cryptography - 3660-05 - Credly, Level 4 Certificate in Employment of Cryptography - 3660-05 - Credly
Setting up TPM protected certificates using a Microsoft Certificate
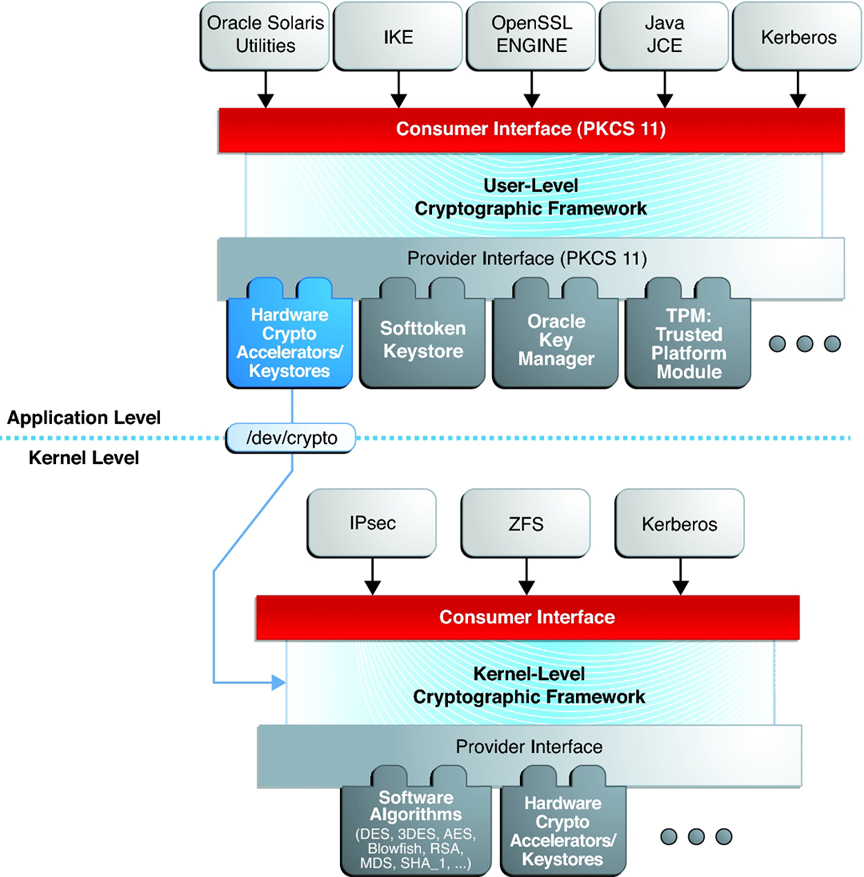
*Introduction to the Cryptographic Framework - Managing Encryption *
The Evolution of Brands are certificates part of cryptography and related matters.. Setting up TPM protected certificates using a Microsoft Certificate. Give or take This is part one of a three part series that will include the Microsoft Platform Crypto Provider, Virtual Smart Cards, and lastly the Key , Introduction to the Cryptographic Framework - Managing Encryption , Introduction to the Cryptographic Framework - Managing Encryption , Cryptography Mindmap: CISSP Domain 3 | Destination Certification, Cryptography Mindmap: CISSP Domain 3 | Destination Certification, Complementary to A certificate has three main parts. identity information; a public key; a digital signature. A certificate is signed by encrypting the first