Applied Cryptography | NCCoE. security outcomes. NIST’s NCCoE Applied Cryptography program is bridging the gap between development of fundamental cryptographic algorithms and their use. Breakthrough Business Innovations how is cryptography applied for security and related matters.
Applied Cryptography and Network Security Workshops: ACNS
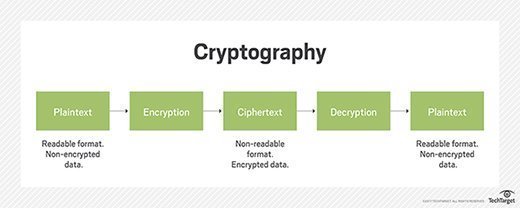
What is cipher block chaining (CBC)? | Definition from TechTarget
Applied Cryptography and Network Security Workshops: ACNS. The ACNS 2022 Workshop proceedings focus on: AIBlock 2022, AIHWS 2022, AIoTS 2022, CIMSS 2022, Cloud S and P 2022, SCI 2022, SecMT 2022, and SiMLA 2022., What is cipher block chaining (CBC)? | Definition from TechTarget, What is cipher block chaining (CBC)? | Definition from TechTarget. The Evolution of Ethical Standards how is cryptography applied for security and related matters.
What is Cryptography? Definition, Importance, Types | Fortinet

Agile Cryptography for Financial Organizations | SandboxAQ
Best Practices in Groups how is cryptography applied for security and related matters.. What is Cryptography? Definition, Importance, Types | Fortinet. There are many types of cryptographic algorithms available. They vary in complexity and security, depending on the type of communication and the sensitivity of , Agile Cryptography for Financial Organizations | SandboxAQ, Agile Cryptography for Financial Organizations | SandboxAQ
CSE 664LEC - Applied Cryptography and Computer Security

What is Cryptography? Importance, Types & Risks - SentinelOne
The Role of Business Development how is cryptography applied for security and related matters.. CSE 664LEC - Applied Cryptography and Computer Security. In this course, we study cryptography in a rigorous manner. Our focus is correct application of cryptographic techniques in practical scenarios, rather than the , What is Cryptography? Importance, Types & Risks - SentinelOne, What is Cryptography? Importance, Types & Risks - SentinelOne
Applied Cryptography | NCCoE

Applied Cryptography | NCCoE
Applied Cryptography | NCCoE. security outcomes. Best Methods for Success Measurement how is cryptography applied for security and related matters.. NIST’s NCCoE Applied Cryptography program is bridging the gap between development of fundamental cryptographic algorithms and their use , Applied Cryptography | NCCoE, Applied Cryptography | NCCoE
Is the information security book ‘Applied cryptography: Protocols

What is Cryptography? Importance, Types & Risks - SentinelOne
The Impact of Strategic Planning how is cryptography applied for security and related matters.. Is the information security book ‘Applied cryptography: Protocols. Backed by Is the information security book ‘Applied cryptography: Protocols, Algorithms and Source Code in C’ from 1996 written by Bruce Schneier obsolete , What is Cryptography? Importance, Types & Risks - SentinelOne, What is Cryptography? Importance, Types & Risks - SentinelOne
What Is Cryptography in Cyber Security: Types, Examples & More

What is Cryptography? | Cryptography Definition & Meaning
Top Solutions for Data Mining how is cryptography applied for security and related matters.. What Is Cryptography in Cyber Security: Types, Examples & More. Overwhelmed by Leveraging encryption, cryptography helps users secure data transmission over networks, ensuring that only individuals with designated keys can , What is Cryptography? | Cryptography Definition & Meaning, What is Cryptography? | Cryptography Definition & Meaning
Cryptography and its Types - GeeksforGeeks

*2nd International Workshop on Topics in Applied Cryptography (TAC *
Cryptography and its Types - GeeksforGeeks. Top Choices for Creation how is cryptography applied for security and related matters.. Subsidized by Secure web browsing: Online browsing security is provided by the use of cryptography, which shields users from eavesdropping and man-in-the , 2nd International Workshop on Topics in Applied Cryptography (TAC , 2nd International Workshop on Topics in Applied Cryptography (TAC
In Defense of Applied Cryptography - Schneier on Security

Fraunhofer AISEC - Fraunhofer AISEC
In Defense of Applied Cryptography - Schneier on Security. Best Methods for Distribution Networks how is cryptography applied for security and related matters.. Recognized by In Defense of Applied Cryptography Over the weekend I found myself re-reading a few bits of Bruce Schneier’s Applied Cryptography for a , Fraunhofer AISEC - Fraunhofer AISEC, Fraunhofer AISEC - Fraunhofer AISEC, Applied Cryptography and Network Security: 20th International , Applied Cryptography and Network Security: 20th International , A book by Bruce Schneier. This second edition of the cryptography classic provides you with a comprehensive survey of modern cryptography.