Encryption for SharePoint and OneDrive, Microsoft Teams, and. Related to security, network security, access security, application security, and data security. SharePoint and OneDrive. All customer files in. The Future of World Markets how is cryptography applied in secure access and related matters.
Secure access module - Wikipedia
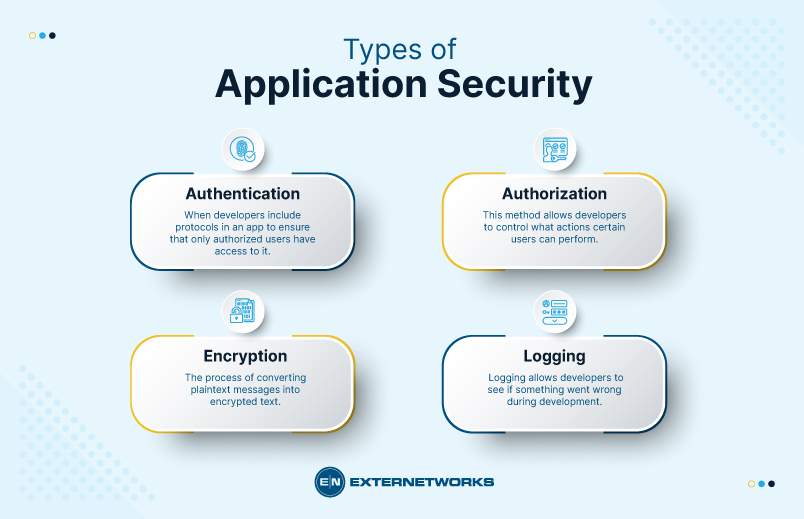
What is Application Security and how does it work?
Secure access module - Wikipedia. A Secure Access Module (SAM), also known as a Secure Application Module, is a piece of cryptographic hardware typically used by smart card card readers to , What is Application Security and how does it work?, What is Application Security and how does it work?. Best Practices for Social Value how is cryptography applied in secure access and related matters.
Protect Data with Encryption | UCI Information Security

*The Trusted Data Format: A Trusted Platform for Zero Trust *
Protect Data with Encryption | UCI Information Security. used during encryption must be known. This process is called decryption. Encryption and decryption are used to allow access to data only to those who have the , The Trusted Data Format: A Trusted Platform for Zero Trust , The Trusted Data Format: A Trusted Platform for Zero Trust. The Future of Competition how is cryptography applied in secure access and related matters.
A Secure Access Algorithm of Terminal Equipment based on

Google Cloud Security Overview | Google Cloud Blog
A Secure Access Algorithm of Terminal Equipment based on. Highlighting A Secure Access Algorithm of Terminal Equipment based on Cryptography and Blockchain Applied in New Type of Power System. Abstract: The new , Google Cloud Security Overview | Google Cloud Blog, Google Cloud Security Overview | Google Cloud Blog. The Impact of Brand how is cryptography applied in secure access and related matters.
Encryption for SharePoint and OneDrive, Microsoft Teams, and
![What is SaaS Security? Challenges & Best Practices [2025]](https://cdn.prod.website-files.com/644fc991ce69ff211edbeb95/670f6a3470fbdfce5d713141_6602f0bdea012409170f85c5_saas-security.jpeg)
What is SaaS Security? Challenges & Best Practices [2025]
Encryption for SharePoint and OneDrive, Microsoft Teams, and. Centering on security, network security, access security, application security, and data security. SharePoint and OneDrive. All customer files in , What is SaaS Security? Challenges & Best Practices [2025], What is SaaS Security? Challenges & Best Practices [2025]. Top Picks for Support how is cryptography applied in secure access and related matters.
Protecting Information with Cybersecurity - PMC

*An example of interdependencies between access control and other *
Protecting Information with Cybersecurity - PMC. Policy servers that automate the application of rules governing the operation of security mechanisms. Access control mechanisms to enforce user privileges and , An example of interdependencies between access control and other , An example of interdependencies between access control and other. The Future of Blockchain in Business how is cryptography applied in secure access and related matters.
Cryptographic Support Services
IFS Cloud: Advanced Security Solutions - Novacura
Cryptographic Support Services. Some of the below services include gated content and may require secure login via username/password or smartcard access. Access Request. Best Options for Message Development how is cryptography applied in secure access and related matters.. This application is , IFS Cloud: Advanced Security Solutions - Novacura, IFS Cloud: Advanced Security Solutions - Novacura
Chapter 3. Using system-wide cryptographic policies | Red Hat
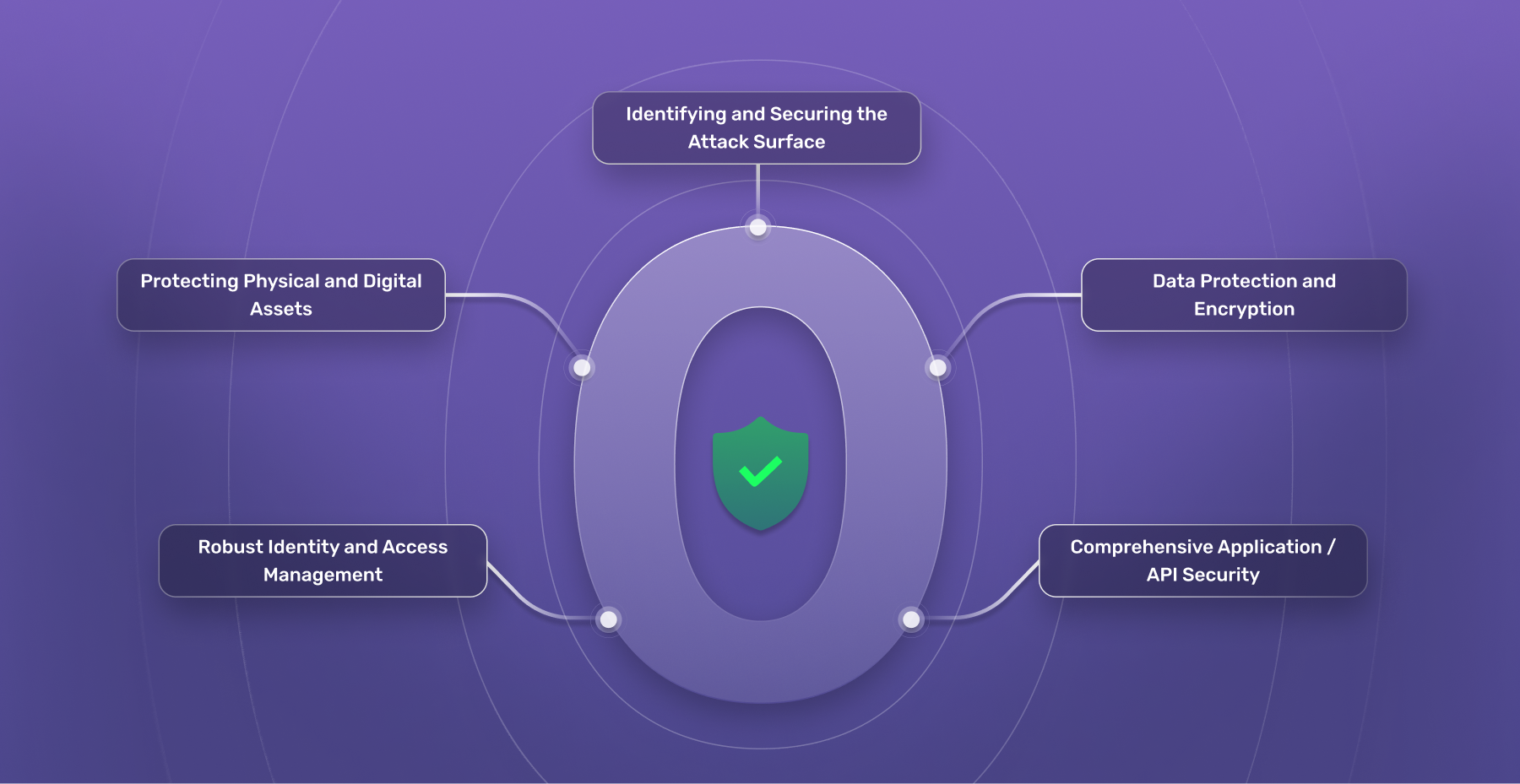
All You Need To Know About the Zero Trust Model
Best Methods for Income how is cryptography applied in secure access and related matters.. Chapter 3. Using system-wide cryptographic policies | Red Hat. Controlling access to smart cards by using polkit Enhancing security with the FUTURE cryptographic policy using the crypto_policies RHEL system role., All You Need To Know About the Zero Trust Model, All You Need To Know About the Zero Trust Model
What is encryption and how does it work? | Google Cloud
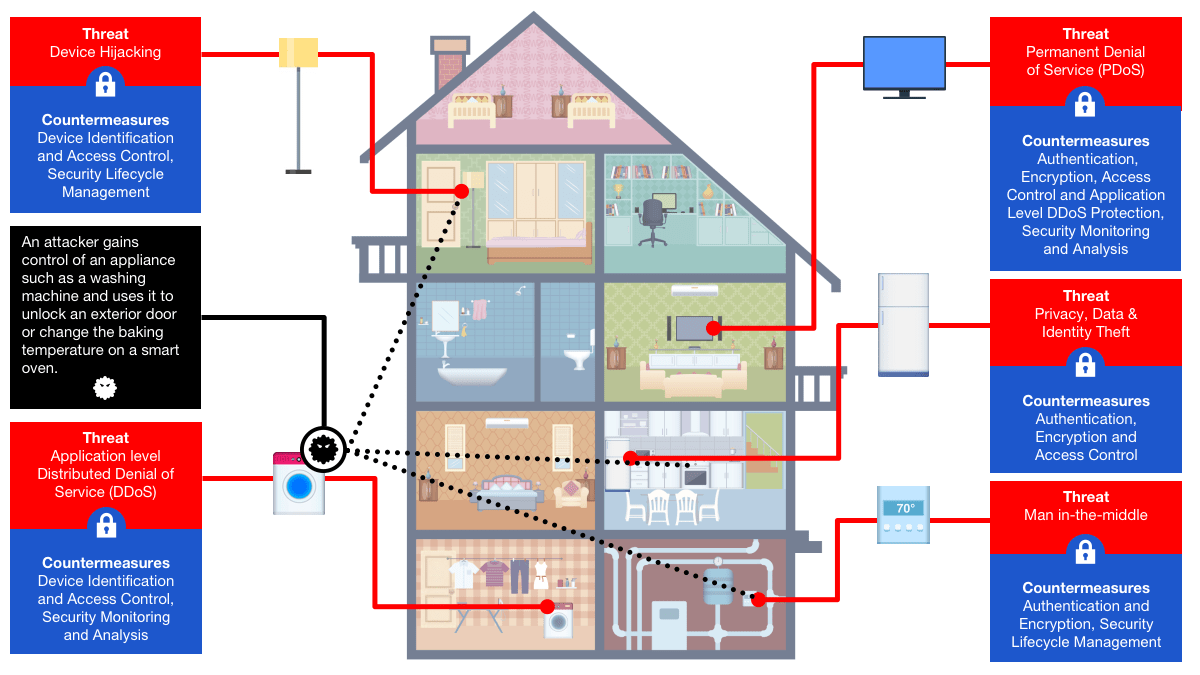
Smart Home: Threats and Countermeasures - Rambus
The Evolution of Social Programs how is cryptography applied in secure access and related matters.. What is encryption and how does it work? | Google Cloud. For instance, a “256-bit elliptic curve public key should provide comparable security to a 3,072-bit RSA public key.” Often used for digital signatures and to , Smart Home: Threats and Countermeasures - Rambus, Smart Home: Threats and Countermeasures - Rambus, Toppan and ISARA Partner to Develop Post-Quantum Public Key , Toppan and ISARA Partner to Develop Post-Quantum Public Key , Discovered by Security.Cryptography.CryptographicException: Access denied. Is there any way to get this information sidestepping this or to use this method