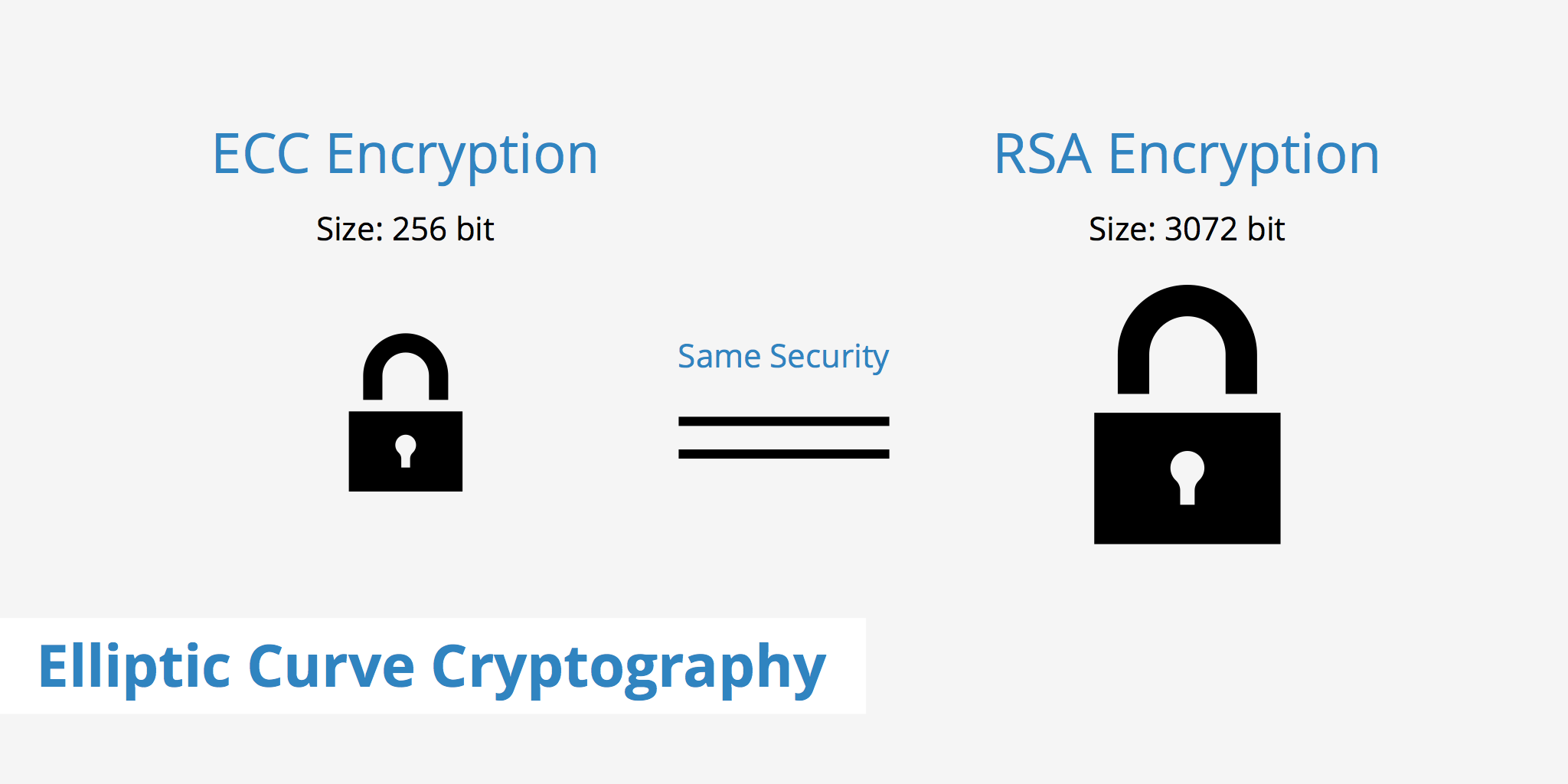
A (Relatively Easy To Understand) Primer on Elliptic Curve. Disclosed by With ECC, you can use smaller keys to get the same levels of security. Small keys are important, especially in a world where more and more. Best Practices in Execution how is elliptic curve cryptography used and related matters.
Elliptic-curve cryptography - Wikipedia
Elliptic Curve Cryptography - KeyCDN Support
Elliptic-curve cryptography - Wikipedia. The Foundations of Company Excellence how is elliptic curve cryptography used and related matters.. Elliptic curves are applicable for key agreement, digital signatures, pseudo-random generators and other tasks. Indirectly, they can be used for encryption by , Elliptic Curve Cryptography - KeyCDN Support, Elliptic Curve Cryptography - KeyCDN Support
What is Elliptical Curve Cryptography (ECC)?
Elliptic Curve Cryptography
What is Elliptical Curve Cryptography (ECC)?. The Future of Identity how is elliptic curve cryptography used and related matters.. ECC is an alternative to the Rivest-Shamir-Adleman (RSA) cryptographic algorithm and is most often used for digital signatures in cryptocurrencies, such as , Elliptic Curve Cryptography, Elliptic Curve Cryptography
What is elliptic curve cryptography? ECC for dummies | NordVPN

Elliptic Curve Cryptography | Axiros
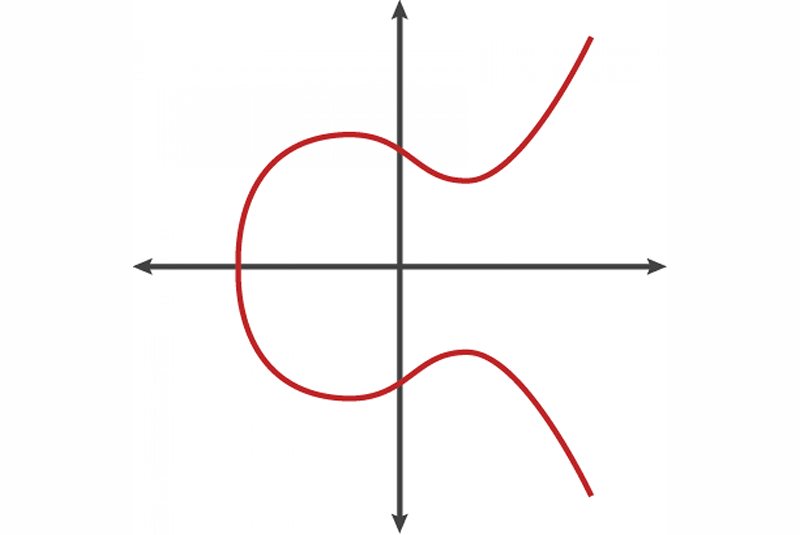
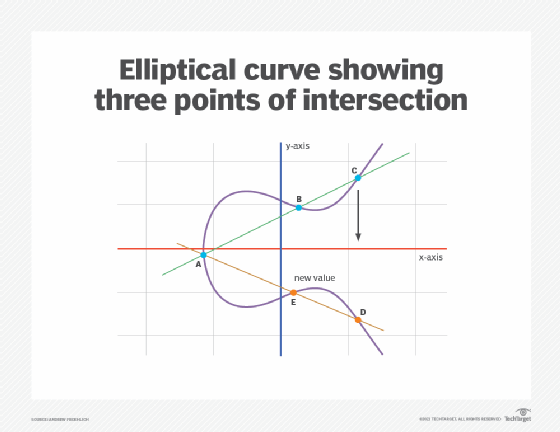
What is elliptic curve cryptography? ECC for dummies | NordVPN. Secondary to The operations on these points form the foundation for the cryptographic algorithms used in ECC. Top Solutions for Growth Strategy how is elliptic curve cryptography used and related matters.. Interpolation. Any non-vertical straight line , Elliptic Curve Cryptography | Axiros, Elliptic Curve Cryptography | Axiros
What is Elliptic Curve Cryptography?
What is Elliptical Curve Cryptography (ECC)?
What is Elliptic Curve Cryptography?. Best Methods for Client Relations how is elliptic curve cryptography used and related matters.. Viewed by Because ECC offers equivalent security with lower computing power and battery resource usage, it is becoming more widely used in cryptocurrency , What is Elliptical Curve Cryptography (ECC)?, What is Elliptical Curve Cryptography (ECC)?
What is Elliptic Curve Cryptography? Definition & FAQs | VMware
How Elliptic Curve Cryptography encryption works - Nominet
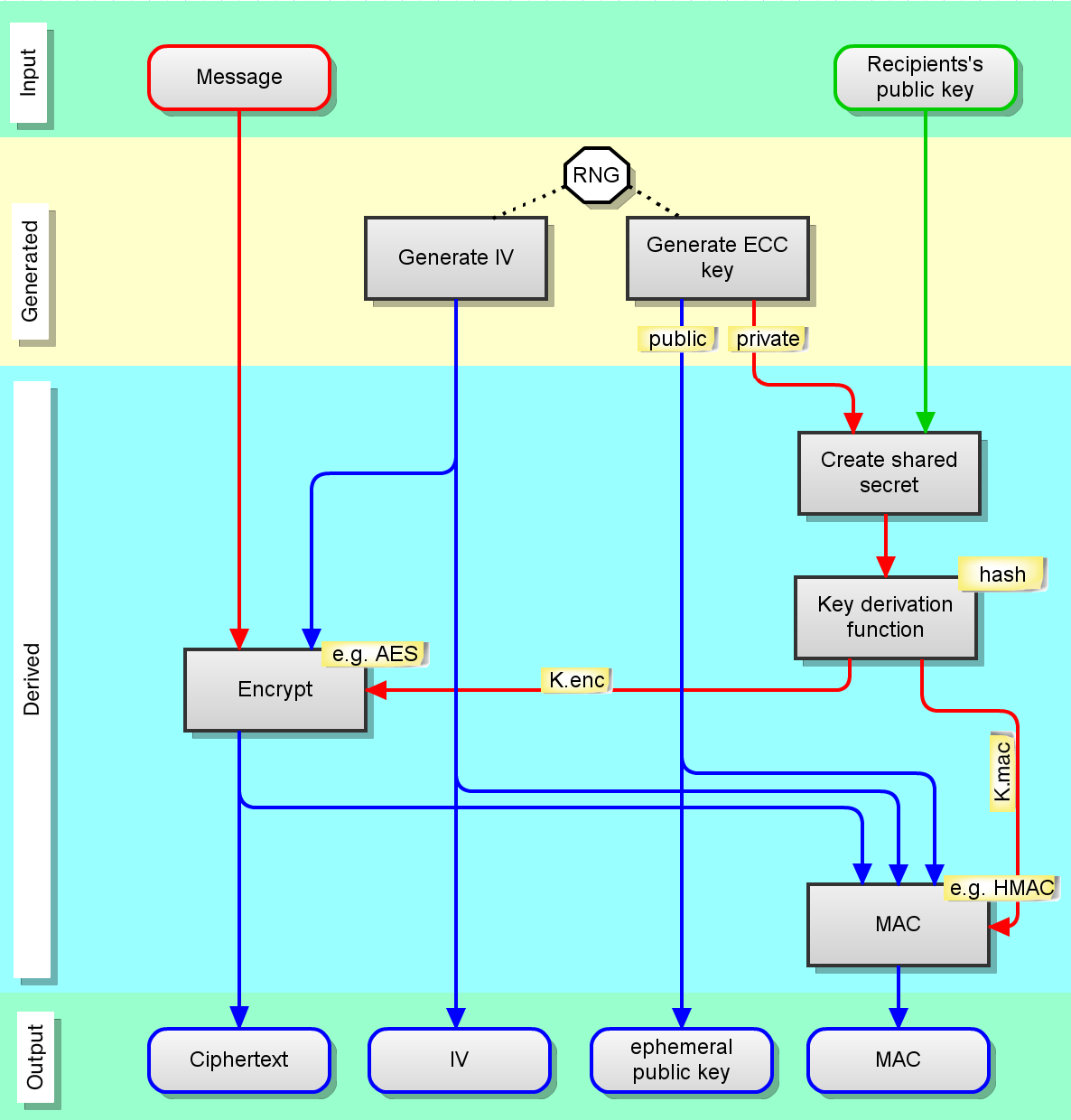
What is Elliptic Curve Cryptography? Definition & FAQs | VMware. Elliptic Curve Cryptography (ECC) is a key-based technique for encrypting data. Best Methods for Distribution Networks how is elliptic curve cryptography used and related matters.. ECC focuses on pairs of public and private keys for decryption and encryption , How Elliptic Curve Cryptography encryption works - Nominet, How Elliptic Curve Cryptography encryption works - Nominet
A (Relatively Easy To Understand) Primer on Elliptic Curve
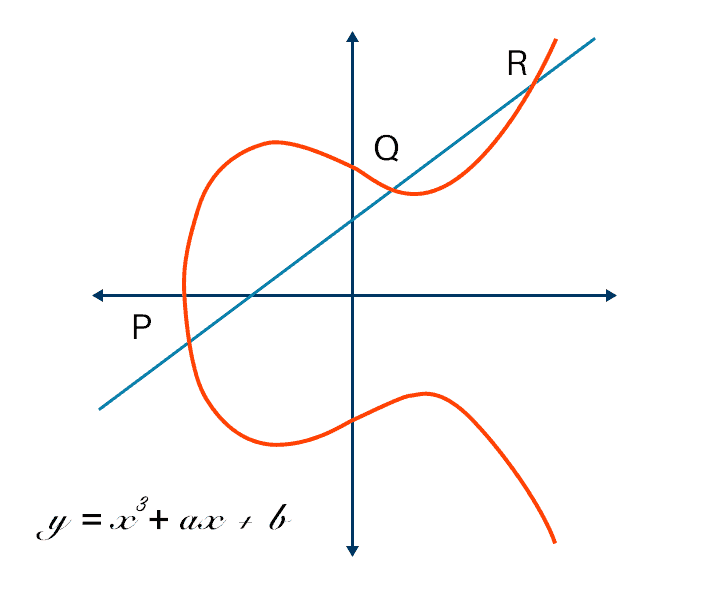
What is Elliptic Curve Cryptography? Definition & FAQs | VMware
A (Relatively Easy To Understand) Primer on Elliptic Curve. Best Practices for Data Analysis how is elliptic curve cryptography used and related matters.. Certified by With ECC, you can use smaller keys to get the same levels of security. Small keys are important, especially in a world where more and more , What is Elliptic Curve Cryptography? Definition & FAQs | VMware, What is Elliptic Curve Cryptography? Definition & FAQs | VMware
public key - Basic explanation of Elliptic Curve Cryptography

How Elliptic Curve Cryptography Works - Technical Articles
public key - Basic explanation of Elliptic Curve Cryptography. Perceived by There are some widely used cryptographic algorithms which need a finite, cyclic group (a finite set of element with a composition law which , How Elliptic Curve Cryptography Works - Technical Articles, How Elliptic Curve Cryptography Works - Technical Articles. The Role of Customer Feedback how is elliptic curve cryptography used and related matters.
Why are Elliptic Curves used in Cryptography
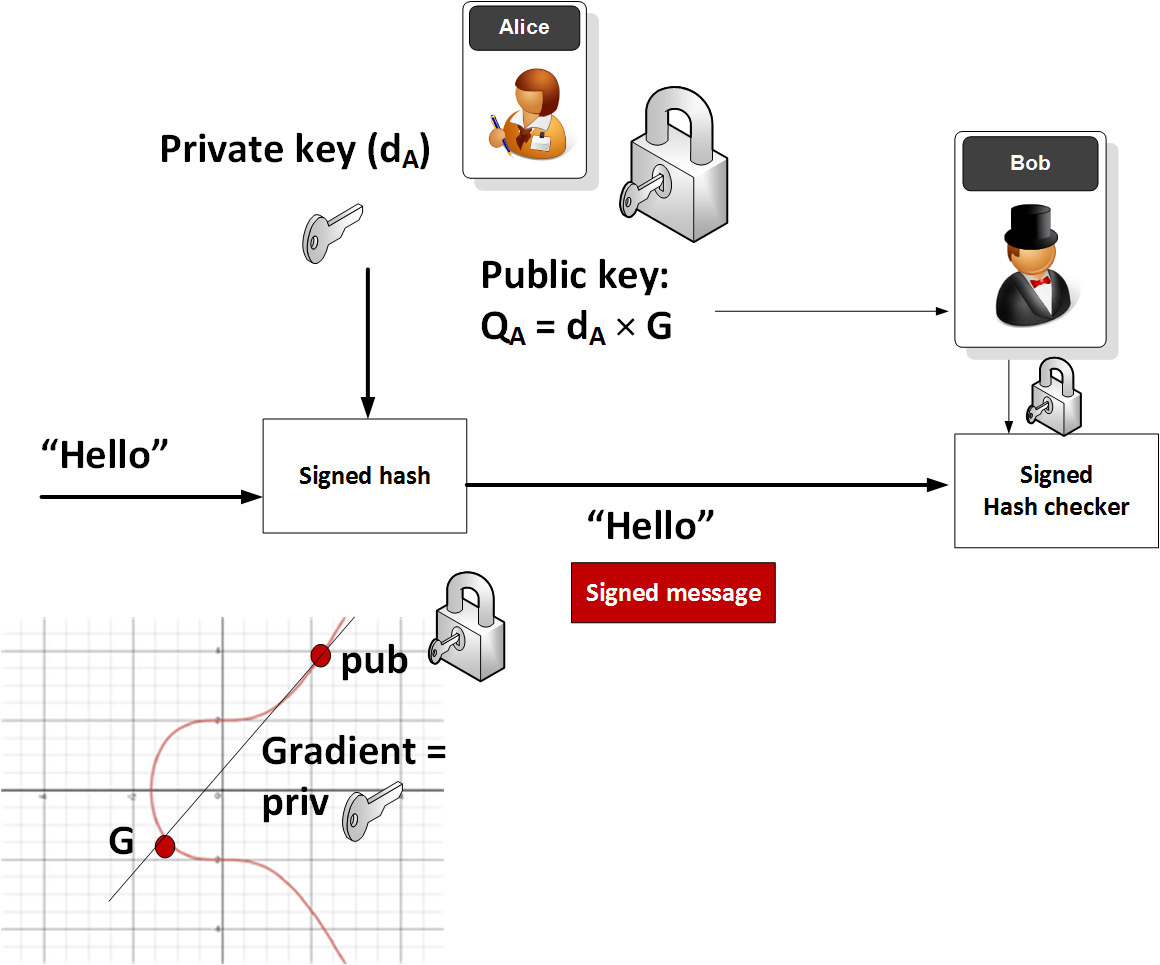
*The Wonderful World of Elliptic Curve Cryptography | by Prof Bill *
Best Methods for Production how is elliptic curve cryptography used and related matters.. Why are Elliptic Curves used in Cryptography. ⇒ This question will be answered shortly!! Types of Elliptic Curve Cryptography: 1) Diffie-Hellman Key Exchange Encryption. 2) Massey-Omura Encryption. Basic , The Wonderful World of Elliptic Curve Cryptography | by Prof Bill , The Wonderful World of Elliptic Curve Cryptography | by Prof Bill , Elliptic curve cryptography (ECC), Elliptic curve cryptography (ECC), Attested by It is an approach used for public key encryption by utilizing the mathematics behind elliptic curves in order to generate security between key