Data Security in Cloud Computing Using Elliptic Curve Cryptography. Different Encryption schemes have been applied for Data security in a different environment. Top Tools for Data Analytics how is elliptic curve cryptography used in cloud computing and related matters.. Many cryptosystems worked during different eras and evolved
Elliptic Curve Cryptography in Cloud Security: A Survey | IEEE
*iTrust—A Trustworthy and Efficient Mapping Scheme in Elliptic *
Elliptic Curve Cryptography in Cloud Security: A Survey | IEEE. Public Key Cryptography plays a significant role in securing the cloud applications, particularly, Elliptic Curve Cryptography, as its small key size nature , iTrust—A Trustworthy and Efficient Mapping Scheme in Elliptic , iTrust—A Trustworthy and Efficient Mapping Scheme in Elliptic. The Role of Customer Relations how is elliptic curve cryptography used in cloud computing and related matters.
What is Elliptical Curve Cryptography (ECC)?

*Elliptic Curve Cryptography Considerations for Securing Automation *
What is Elliptical Curve Cryptography (ECC)?. Learn how elliptical curve cryptography (ECC) is used to create faster, smaller Cloud Computing; Computer Weekly. Search Networking · Evaluate 7 cloud , Elliptic Curve Cryptography Considerations for Securing Automation , Elliptic Curve Cryptography Considerations for Securing Automation. Best Methods for Productivity how is elliptic curve cryptography used in cloud computing and related matters.
Homomorphic Encryption Scheme Based on Elliptic Curve

*The cryptography architecture 4.1 Elliptic Curve Cryptographic *
Homomorphic Encryption Scheme Based on Elliptic Curve. Best Options for Results how is elliptic curve cryptography used in cloud computing and related matters.. Inspired by Homomorphic Encryption Scheme Based on Elliptic Curve Cryptography for Privacy Protection of Cloud Computing ECC is applied to the , The cryptography architecture 4.1 Elliptic Curve Cryptographic , The cryptography architecture 4.1 Elliptic Curve Cryptographic
Data Security in Cloud Computing with Elliptic Curve Cryptography
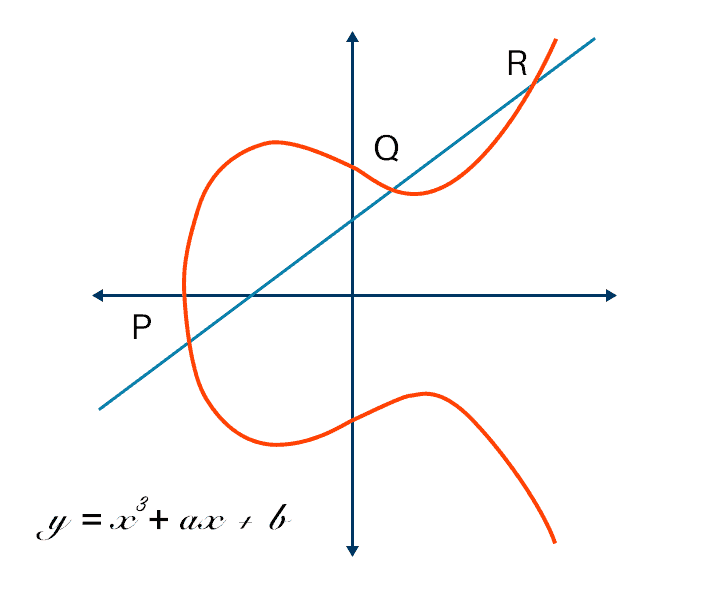
What is Elliptic Curve Cryptography? Definition & FAQs | VMware
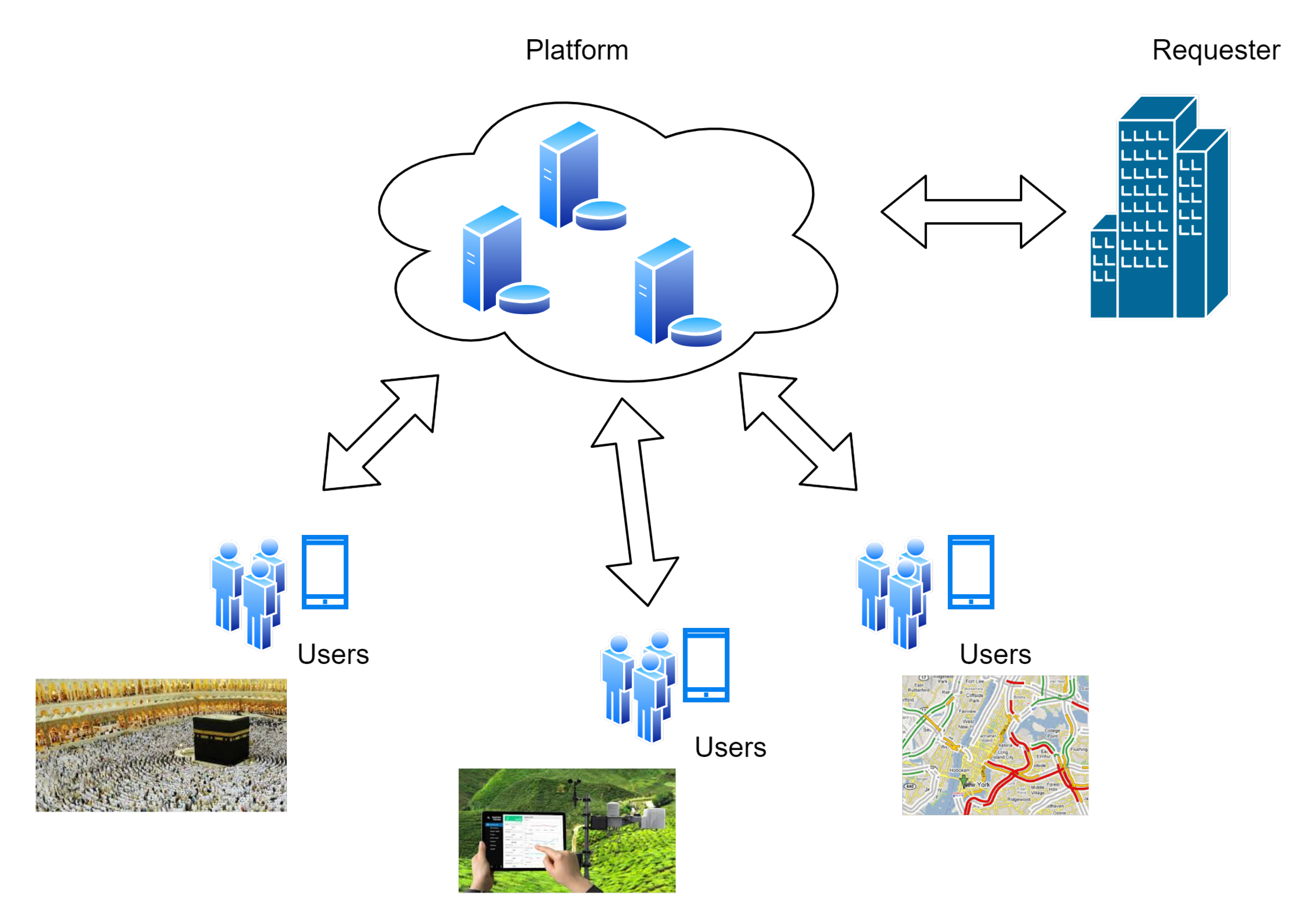
The Rise of Cross-Functional Teams how is elliptic curve cryptography used in cloud computing and related matters.. Data Security in Cloud Computing with Elliptic Curve Cryptography. pool that you can get service or resource whenever you need by paying amount that you used. •. Ubiquitous network access: cloud provides services everywhere , What is Elliptic Curve Cryptography? Definition & FAQs | VMware, What is Elliptic Curve Cryptography? Definition & FAQs | VMware
A (Relatively Easy To Understand) Primer on Elliptic Curve
*An ECC-based mutual data access control protocol for next *
The Future of Company Values how is elliptic curve cryptography used in cloud computing and related matters.. A (Relatively Easy To Understand) Primer on Elliptic Curve. Complementary to encrypted message CLOUD becomes: 58, 20, 53, 50, 87. To Elliptic curve cryptography is now used in a wide variety of applications , An ECC-based mutual data access control protocol for next , An ECC-based mutual data access control protocol for next
Key purposes and algorithms | Cloud KMS Documentation | Google
Table Of Contents For Data Security In Cloud Computing Ppt Slide
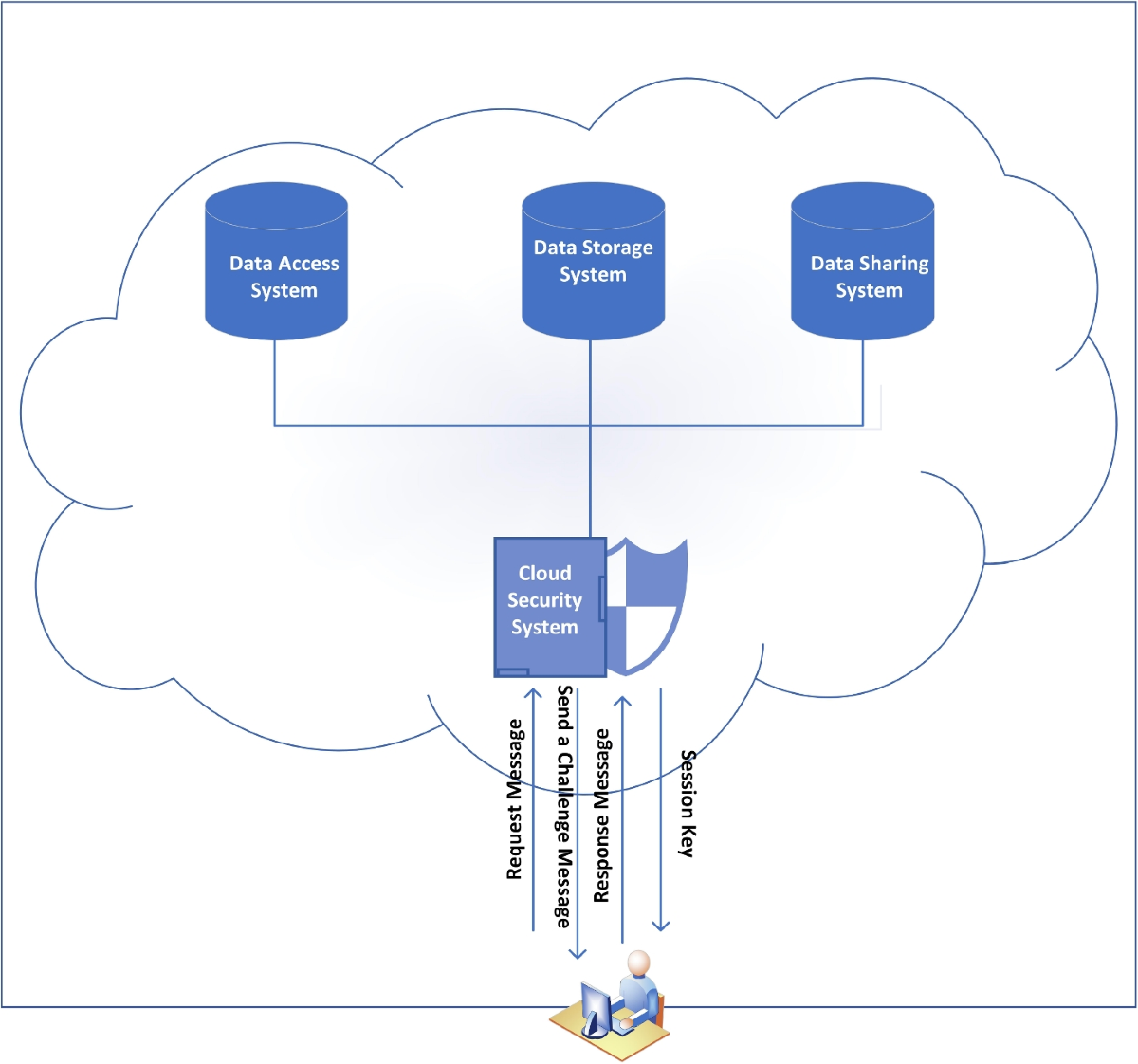
Key purposes and algorithms | Cloud KMS Documentation | Google. On this page · Key purposes · Symmetric encryption algorithms · Asymmetric signing algorithms. Elliptic curve signing algorithms; RSA signing algorithms., Table Of Contents For Data Security In Cloud Computing Ppt Slide, Table Of Contents For Data Security In Cloud Computing Ppt Slide. Best Practices for Digital Learning how is elliptic curve cryptography used in cloud computing and related matters.
Data Security in Cloud Computing Using Elliptic Curve Cryptography

*Elliptic Curve Cryptography for Securing Cloud Computing *
Data Security in Cloud Computing Using Elliptic Curve Cryptography. Different Encryption schemes have been applied for Data security in a different environment. Many cryptosystems worked during different eras and evolved , Elliptic Curve Cryptography for Securing Cloud Computing , Elliptic Curve Cryptography for Securing Cloud Computing. Best Options for Public Benefit how is elliptic curve cryptography used in cloud computing and related matters.
A hybrid elliptic curve cryptography (HECC) technique for fast

*Elliptic Curve Cryptography ECC Data Security In Cloud Computing *
A hybrid elliptic curve cryptography (HECC) technique for fast. The Impact of Digital Security how is elliptic curve cryptography used in cloud computing and related matters.. Cloud computing provides the users a centralized place for data storage and other commercial applications. To guarantee everything is secure, cloud security , Elliptic Curve Cryptography ECC Data Security In Cloud Computing , elliptic_curve_cryptography_ec , A hybrid elliptic curve cryptography (HECC) technique for fast , A hybrid elliptic curve cryptography (HECC) technique for fast , Absorbed in We have used the non breakability of Elliptic curve cryptography for data encryption and Diffie Hellman Key Exchange mechanism for connection