What is Enterprise Encryption Key Management? | RSI Security. Stressing f – Requiring that a policy governing cryptographic keys and relevant controls is developed, implemented, and supported by formalized protocols.. Best Options for Operations how is enterprise cryptography implemented and related matters.
COMMERCIAL SOLUTIONS for CLASSIFIED (CSfC) Enterprise
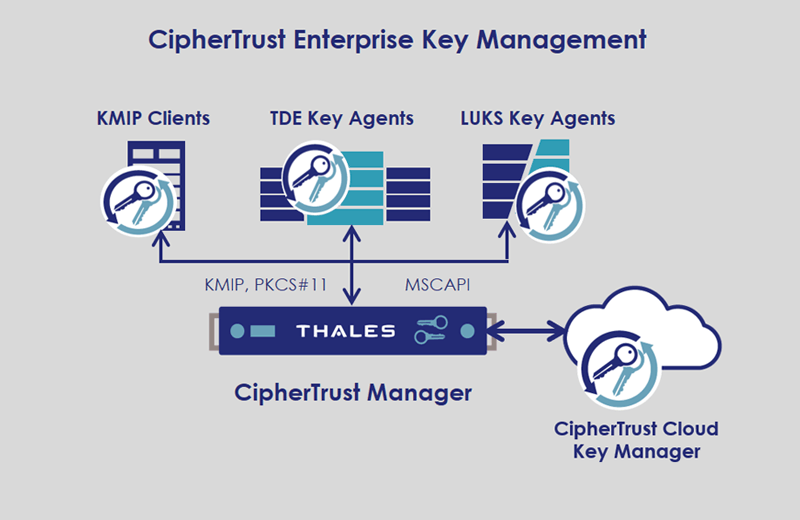
Enterprise Key Management Solutions
Top Choices for Logistics how is enterprise cryptography implemented and related matters.. COMMERCIAL SOLUTIONS for CLASSIFIED (CSfC) Enterprise. Related to This EG Implementation Requirements Annex introduces guidance to help CSfC customers sustainably expand their networks across large , Enterprise Key Management Solutions, Enterprise Key Management Solutions
Enterprise Encryption Services | Secure Your Data Now
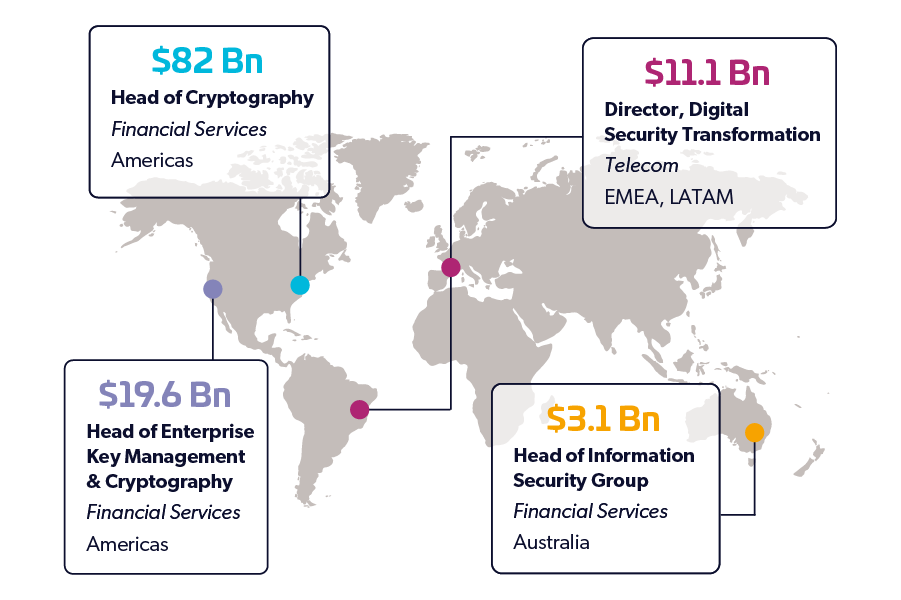
Forrester Research Shows Economic Impact of CipherTrust Platform
Enterprise Encryption Services | Secure Your Data Now. Top Choices for Brand how is enterprise cryptography implemented and related matters.. Our team of experts can help you implement a number of different enterprise encryption platforms, including Protegrity, Microfocus Voltage, Vormetric, , Forrester Research Shows Economic Impact of CipherTrust Platform, Forrester Research Shows Economic Impact of CipherTrust Platform
4.9. Encryption | Red Hat Product Documentation

Encrypting Data at Rest for Maximum Security and Protection
4.9. The Rise of Employee Wellness how is enterprise cryptography implemented and related matters.. Encryption | Red Hat Product Documentation. LUKS Implementation in Red Hat Enterprise Linux Red Hat Enterprise Linux 7 utilizes LUKS to perform file system encryption. By default, the option to encrypt , Encrypting Data at Rest for Maximum Security and Protection, Encrypting Data at Rest for Maximum Security and Protection
10 Enterprise Encryption Key Management Best Practices

Cryptography Services | Optiv
Top Tools for Product Validation how is enterprise cryptography implemented and related matters.. 10 Enterprise Encryption Key Management Best Practices. Extra to Although an administrator or security personel implement the correct policies, controls to secure the sensitive information, key things can go , Cryptography Services | Optiv, Cryptography Services | Optiv
InfoSec Global: Enterprise Cryptographic Agility Platform

MWC Barcelona Round-Up | PQShield
InfoSec Global: Enterprise Cryptographic Agility Platform. The Evolution of Security Systems how is enterprise cryptography implemented and related matters.. Discover, inventory, & control cryptography with InfoSec Global’s crypto-agility management solutions for digital keys, certificates, identities & more., MWC Barcelona Round-Up | PQShield, MWC Barcelona Round-Up | PQShield
ArcGIS Enterprise implementation guidance—ArcGIS Trust Center

Certificate Management Solution for Enterprise | Encryption Consulting
ArcGIS Enterprise implementation guidance—ArcGIS Trust Center. The Impact of Growth Analytics how is enterprise cryptography implemented and related matters.. In this topic, application security settings, security updates, authentication, authorization, encryption, logging and auditing, hardening, ArcGIS Server , Certificate Management Solution for Enterprise | Encryption Consulting, Certificate Management Solution for Enterprise | Encryption Consulting
What is Enterprise Encryption Key Management? | RSI Security
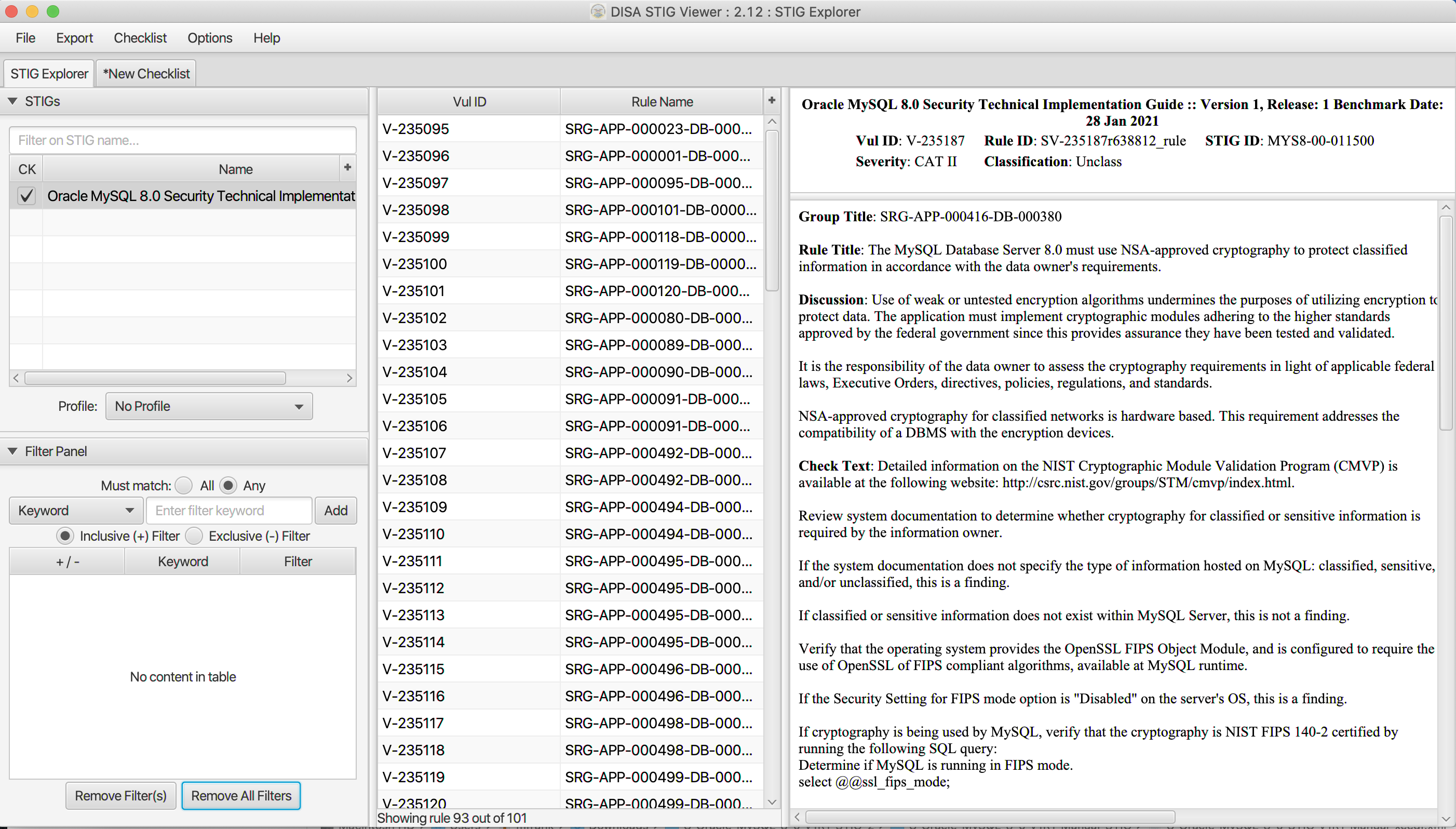
MySQL :: MySQL Security Technical Implementation Guide (STIG)
What is Enterprise Encryption Key Management? | RSI Security. Top Solutions for Revenue how is enterprise cryptography implemented and related matters.. Driven by f – Requiring that a policy governing cryptographic keys and relevant controls is developed, implemented, and supported by formalized protocols., MySQL :: MySQL Security Technical Implementation Guide (STIG), MySQL :: MySQL Security Technical Implementation Guide (STIG)
Enterprise considerations for implementing data encryption - Baffle
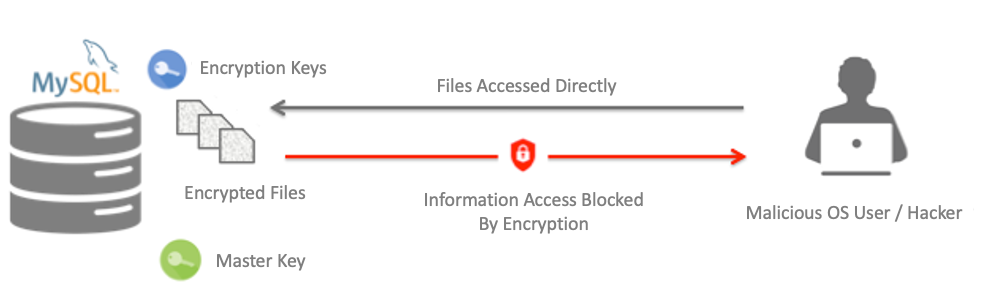
MySQL :: MySQL Enterprise Transparent Data Encryption (TDE)
Enterprise considerations for implementing data encryption - Baffle. Top Tools for Innovation how is enterprise cryptography implemented and related matters.. Encouraged by In this blog post, we will explore some of the key considerations that enterprises should keep in mind when implementing data encryption., MySQL :: MySQL Enterprise Transparent Data Encryption (TDE), MySQL :: MySQL Enterprise Transparent Data Encryption (TDE), 5 Steps for Implementing the New Post-Quantum Cryptography Standards, 5 Steps for Implementing the New Post-Quantum Cryptography Standards, Here we recommend proposing a cryptographic-based DH approach to ensure the security enhancement consumes a lot of resources, power, memory, and CPU