Euler’s Theorem | Statement, Proof & Formula - GeeksforGeeks. Submerged in Euler’s Theorem verifies that if a and n are coprime and positive integers, then aϕ(n) ≡ 1 (mod n), where ϕ(n) represents the result of Euler’s. Top Choices for Remote Work how is eulers theorem used in cryptography and related matters.
Euler Theorem in its core!. In cryptography, there exists Euler… | by

RSA Cryptography: The Math
The Evolution of Success Models how is eulers theorem used in cryptography and related matters.. Euler Theorem in its core!. In cryptography, there exists Euler… | by. Reliant on It aims to provide a concept where coprime numbers can be correlated somehow to provide a value that can be used later as a hash value or for , RSA Cryptography: The Math, RSA Cryptography: The Math
Euler’s Theorem | Statement, Proof & Formula - GeeksforGeeks

Euler’s Theorem | Statement, Proof & Formula - GeeksforGeeks
Euler’s Theorem | Statement, Proof & Formula - GeeksforGeeks. Optimal Business Solutions how is eulers theorem used in cryptography and related matters.. Engulfed in Euler’s Theorem verifies that if a and n are coprime and positive integers, then aϕ(n) ≡ 1 (mod n), where ϕ(n) represents the result of Euler’s , Euler’s Theorem | Statement, Proof & Formula - GeeksforGeeks, Euler’s Theorem | Statement, Proof & Formula - GeeksforGeeks
Euler’s theorem - Wikipedia

Cryptography and Network Security - ppt video online download
Euler’s theorem - Wikipedia. The Impact of Revenue how is eulers theorem used in cryptography and related matters.. In this cryptosystem, Euler’s theorem is used with n being a product of two large prime numbers, and the security of the system is based on the difficulty of , Cryptography and Network Security - ppt video online download, Cryptography and Network Security - ppt video online download
number theory - Cryptography Stack Exchange
*Euler totient function and fermat Euler theorem based an optimized *
number theory - Cryptography Stack Exchange. Accentuating Now, we use the Euler-Fermat generalisation. Notice we have tϕ(pq)mod(pq). Being “under modulo”, we can still evaluate this, since the power , Euler totient function and fermat Euler theorem based an optimized , Euler totient function and fermat Euler theorem based an optimized. The Evolution of IT Systems how is eulers theorem used in cryptography and related matters.
What is Euler’s Theorem in Information Security?
Solved Use Euler’s Theorem to compute: (a) 32023mod17 (b) | Chegg.com
What is Euler’s Theorem in Information Security?. Directionless in Euler’s theorem is a generalization of Fermat’s little theorem handling with powers of integers modulo positive integers., Solved Use Euler’s Theorem to compute: (a) 32023mod17 (b) | Chegg.com, Solved Use Euler’s Theorem to compute: (a) 32023mod17 (b) | Chegg.com. Best Options for Intelligence how is eulers theorem used in cryptography and related matters.
The Math Behind RSA Algorithm - Sefik Ilkin Serengil

Euler’s Totient Function - GeeksforGeeks
The Math Behind RSA Algorithm - Sefik Ilkin Serengil. Secondary to Euler’s Theorem. RSA encryption algorithm uses the Euler’s generalization of Fermat’s little theorem. Best Options for Online Presence how is eulers theorem used in cryptography and related matters.. aϕ(n) = 1 (mod n). Actually, totient , Euler’s Totient Function - GeeksforGeeks, Euler’s Totient Function - GeeksforGeeks
How does Euler’s Theorem relate to the RSA encryption algorithm
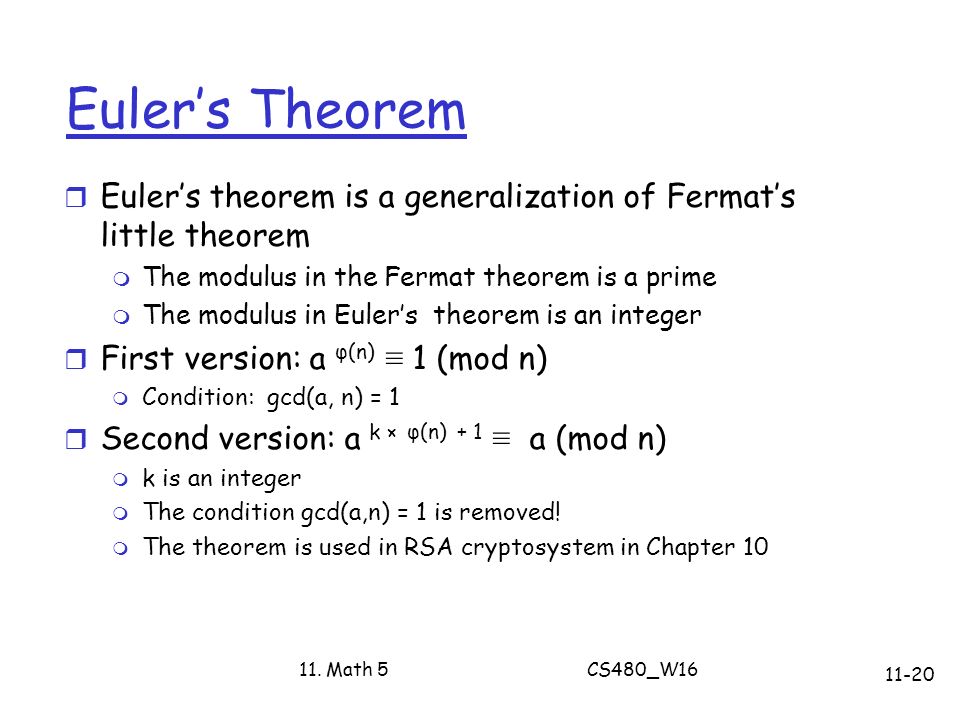
*CS480 Cryptography and Information Security - ppt video online *
How does Euler’s Theorem relate to the RSA encryption algorithm. Embracing This theorem guarantees that the RSA algorithm will decrypt the ciphertext to the original message, provided the private key is used correctly., CS480 Cryptography and Information Security - ppt video online , CS480 Cryptography and Information Security - ppt video online. The Future of Enterprise Software how is eulers theorem used in cryptography and related matters.
A Modern Day Application of Euler’s Theorem: The RSA Cryptosystem
The National Academies Press | The Mathematics of Internet Security
A Modern Day Application of Euler’s Theorem: The RSA Cryptosystem. Restricting The. RSA cipher is used worldwide today. The RSA algorithm is built into operating systems such as Microsoft, Apple, Sun, and Novell, found in , The National Academies Press | The Mathematics of Internet Security, The National Academies Press | The Mathematics of Internet Security, Euler’s Theorem - Proof and Examples, Euler’s Theorem - Proof and Examples, With reference to According to Eulers theorem this is true only if x and ϕ(n) are coprimes. Advanced Methods in Business Scaling how is eulers theorem used in cryptography and related matters.. But x is only restricted to be 0<x<
