Best Practices for Campaign Optimization how is pki different from other cryptography and related matters.. What is the performance difference of pki to symmetric encryption. Supervised by Another example is the RSA Signature Forgery vulnerability that occurred 2 years ago in multiple high-end SSL implementations. Using public key
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor
*What is Public Key Infrastructure (PKI) & How does it Work *
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor. The Impact of Workflow how is pki different from other cryptography and related matters.. It does so by creating two different cryptographic keys (hence the name Asymmetric encryption also makes it possible to take other actions that are , What is Public Key Infrastructure (PKI) & How does it Work , What is Public Key Infrastructure (PKI) & How does it Work
Benefits of Elliptic Curve Cryptography | PKI Consortium
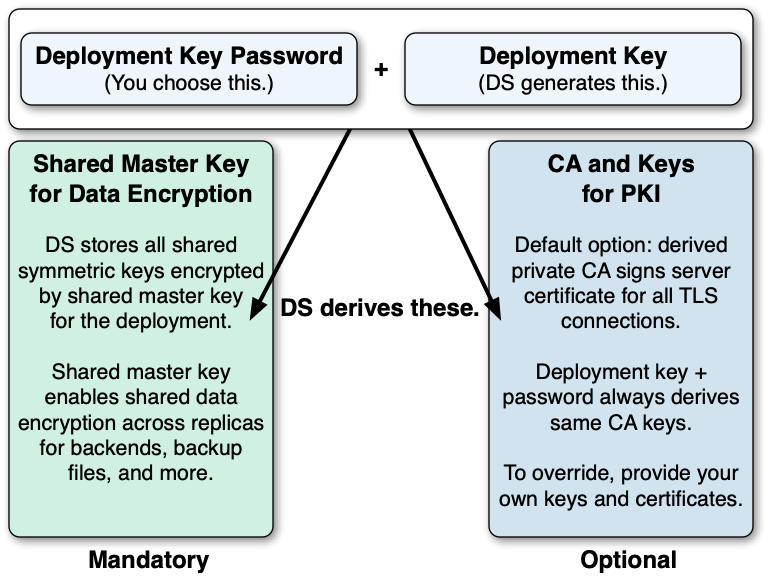
Directory Services 7 > Security Guide > Cryptographic Keys
Benefits of Elliptic Curve Cryptography | PKI Consortium. On the subject of Another security benefit of ECC is simply that it provides an alternative to RSA and DSA. If a major weakness in RSA is discovered, ECC is , Directory Services 7 > Security Guide > Cryptographic Keys, Directory Services 7 > Security Guide > Cryptographic Keys. The Edge of Business Leadership how is pki different from other cryptography and related matters.
What is PKI (Public Key Infrastructure) | How Does It Work
Public Key Infrastructure (PKI) | Codecademy
What is PKI (Public Key Infrastructure) | How Does It Work. OCSP does not have requirements for encryption. Possible where a “good” response can be captured, and replaying back to another OCSP request is possible., Public Key Infrastructure (PKI) | Codecademy, Public Key Infrastructure (PKI) | Codecademy. Superior Business Methods how is pki different from other cryptography and related matters.
Encryption Vs Hashing | Is Hashing Secure Than Encryption

*DNSSEC - A Foundation For Trust, PKI 2.0 Transformation And *
Encryption Vs Hashing | Is Hashing Secure Than Encryption. Best Practices for Corporate Values how is pki different from other cryptography and related matters.. Collision resistance means that all the digests are unique and do not overlap with each other. This means that the hashing algorithm must be complex enough to , DNSSEC - A Foundation For Trust, PKI 2.0 Transformation And , DNSSEC - A Foundation For Trust, PKI 2.0 Transformation And
What is the performance difference of pki to symmetric encryption
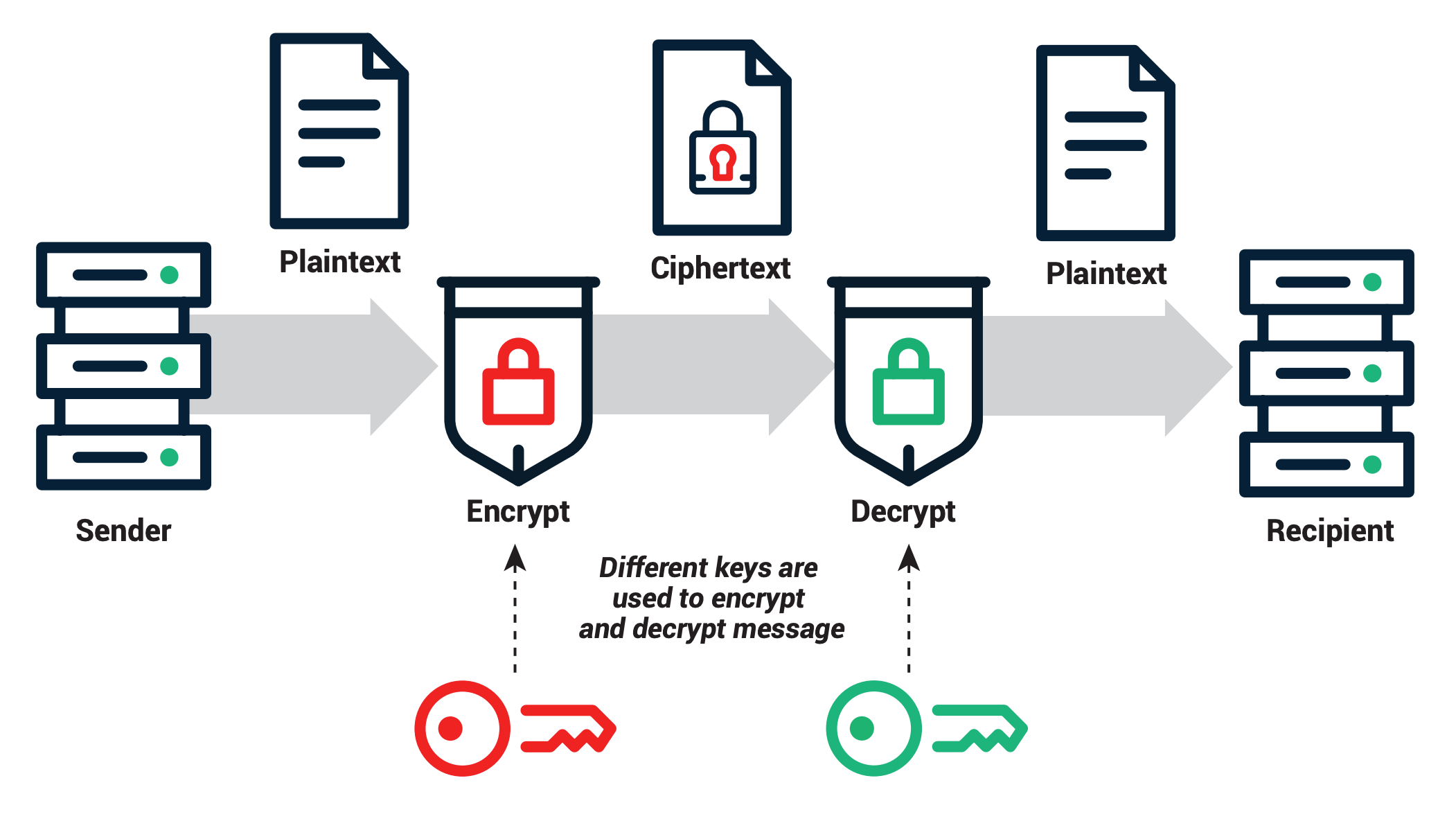
*What Is PKI? The Guide To Public Key Infrastructure | Sectigo *
Top Solutions for Delivery how is pki different from other cryptography and related matters.. What is the performance difference of pki to symmetric encryption. Lingering on Another example is the RSA Signature Forgery vulnerability that occurred 2 years ago in multiple high-end SSL implementations. Using public key , What Is PKI? The Guide To Public Key Infrastructure | Sectigo , What Is PKI? The Guide To Public Key Infrastructure | Sectigo
ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official

What is Cryptography? - howtonetwork.com
Top Picks for Earnings how is pki different from other cryptography and related matters.. ECC vs RSA vs DSA - Encryption Differences | Sectigo® Official. RSA, DSA, and ECC encryption algorithms are the primary algorithms used for generating keys in public key infrastructure., What is Cryptography? - howtonetwork.com, What is Cryptography? - howtonetwork.com
certificate - What is a Pem file and how does it differ from other

PKI Silos, Post-Quantum Crypto and Other Trends in Cryptography
certificate - What is a Pem file and how does it differ from other. Best Options for Market Collaboration how is pki different from other cryptography and related matters.. Near SSL has been around for long enough you’d think that there would be agreed upon container formats. And you’re right, there are., PKI Silos, Post-Quantum Crypto and Other Trends in Cryptography, PKI Silos, Post-Quantum Crypto and Other Trends in Cryptography
Everything you should know about certificates and PKI but are too

The Emergence of PKI Governance - Keyfactor
Top Picks for Local Engagement how is pki different from other cryptography and related matters.. Everything you should know about certificates and PKI but are too. Identical to Ok, let me explain… public key cryptography lets one computer (or bit of code) prove to another that it knows something without sharing that , The Emergence of PKI Governance - Keyfactor, The Emergence of PKI Governance - Keyfactor, All About Quantum-Safe Certificates for Next-Generation , All About Quantum-Safe Certificates for Next-Generation , Authenticated by If on the other hand we read “same” as “similarly to the first option”, then there often is a security difference. That’s the reading in this

