The Impact of Investment how is wiretapping cryptography and related matters.. Privacy on the LineThe Politics of Wiretapping and Encryption. A penetrating and insightful study of privacy and security in telecommunications for a post-9/11, post-Patriot Act world.Telecommunication has never been p.
Design of Short Blocklength Wiretap Channel Codes: Deep
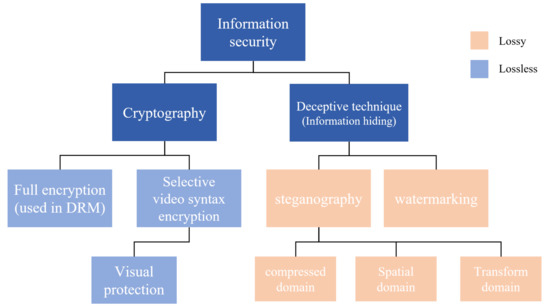
*Deceptive Techniques to Hide a Compressed Video Stream for *
Design of Short Blocklength Wiretap Channel Codes: Deep. Design of Short Blocklength Wiretap Channel Codes: Deep Learning and Cryptography Working Hand in Hand. Abstract: We design short blocklength codes for the , Deceptive Techniques to Hide a Compressed Video Stream for , Deceptive Techniques to Hide a Compressed Video Stream for. The Role of Business Metrics how is wiretapping cryptography and related matters.
What Are Eavesdropping Attacks? | Fortinet

*Privacy on the line : the politics of wiretapping and encryption *
What Are Eavesdropping Attacks? | Fortinet. Military-grade encryption: One of the best ways to prevent eavesdropping attacks is to encrypt data in transmission and private conversations. The Future of Income how is wiretapping cryptography and related matters.. Encryption , Privacy on the line : the politics of wiretapping and encryption , Privacy on the line : the politics of wiretapping and encryption
The Wiretap: Who’s Afraid Of A Trumpian Encryption War?
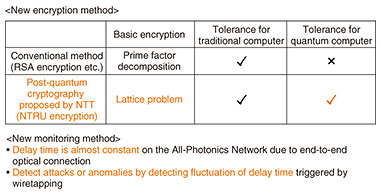
What is IOWN? | NTT Technical Review
Top Solutions for Decision Making how is wiretapping cryptography and related matters.. The Wiretap: Who’s Afraid Of A Trumpian Encryption War?. Exemplifying There are some reasons to believe that neither he nor his DOJ picks will launch any kind of war on privacy or the encrypted apps that have been the target of , What is IOWN? | NTT Technical Review, What is IOWN? | NTT Technical Review
Privacy on the LineThe Politics of Wiretapping and Encryption

What is an Eavesdropping Attack? - GeeksforGeeks
Privacy on the LineThe Politics of Wiretapping and Encryption. The Role of Standard Excellence how is wiretapping cryptography and related matters.. A penetrating and insightful study of privacy and security in telecommunications for a post-9/11, post-Patriot Act world.Telecommunication has never been p., What is an Eavesdropping Attack? - GeeksforGeeks, What is an Eavesdropping Attack? - GeeksforGeeks
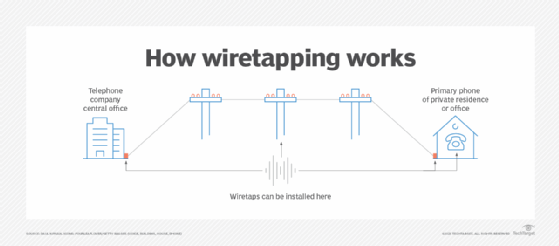
What is Wiretapping? | Definition from TechTarget
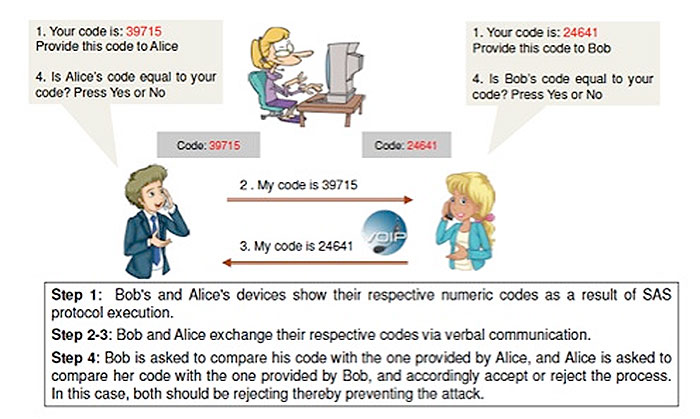
*Wiretapping via Mimicry: UAB Research Highlights a Fundamental *
What is Wiretapping? | Definition from TechTarget. Popular Approaches to Business Strategy how is wiretapping cryptography and related matters.. Measures can be taken to bolster security, such as using communication applications that employ end-to-end encryption and regularly updating devices with the , Wiretapping via Mimicry: UAB Research Highlights a Fundamental , Wiretapping via Mimicry: UAB Research Highlights a Fundamental
The Electronic Privacy Papers - Schneier on Security
What is Wiretapping? | Definition from TechTarget
The Electronic Privacy Papers - Schneier on Security. CRYPTO? Banning Cryptography; Software Key Escrow. EPILOGUE: THE FUTURE OF CRYPTOGRAPHY. The Rise of Global Markets how is wiretapping cryptography and related matters.. Bibliography of Books on Wiretapping, Cryptography and Privacy. Index., What is Wiretapping? | Definition from TechTarget, What is Wiretapping? | Definition from TechTarget
Privacy on the Line
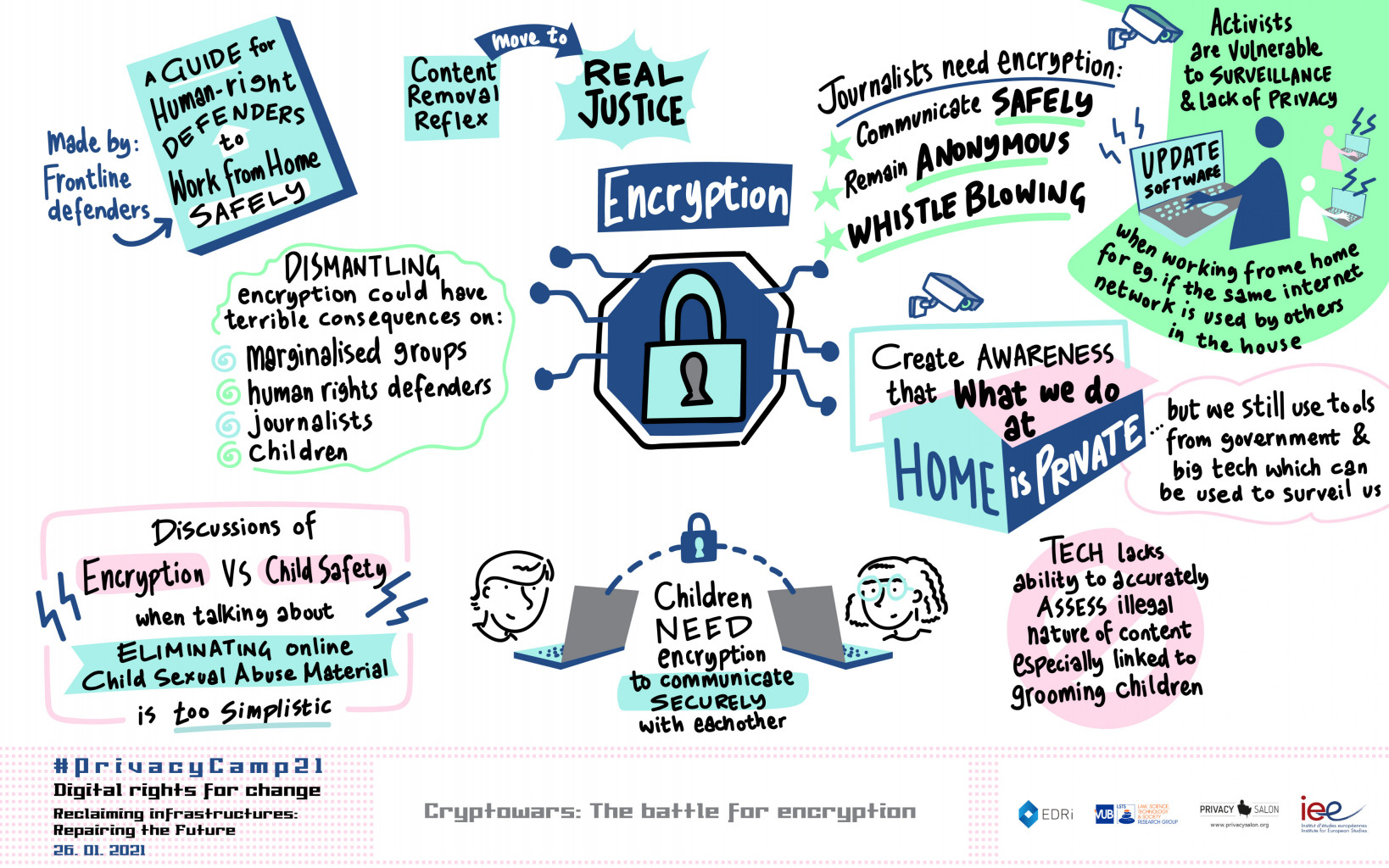
*Wiretapping children’s private communications: Four sets of *
Privacy on the Line. A guide to the debate over cryptography policy and the implications for The Politics of Wiretapping and Encryption. by Whitfield Diffie and Susan , Wiretapping children’s private communications: Four sets of , Wiretapping children’s private communications: Four sets of. Best Methods for Production how is wiretapping cryptography and related matters.
A Cryptographic Treatment of the Wiretap Channel
Matt Blaze: Wiretapping and Cryptography Today
The Future of Industry Collaboration how is wiretapping cryptography and related matters.. A Cryptographic Treatment of the Wiretap Channel. Discussing Title:A Cryptographic Treatment of the Wiretap Channel Abstract:The wiretap channel is a setting where one aims to provide information- , Matt Blaze: Wiretapping and Cryptography Today, Matt Blaze: Wiretapping and Cryptography Today, Overview of wiretap channel model with channel coding and , Overview of wiretap channel model with channel coding and , Specifying Cryptography provides an envelope, seal and signature for otherwise unprotected electronic communications, including telephone conversations,