What is Cryptography? Definition, Importance, Types | Fortinet. Cryptography also secures browsing, such as with virtual private networks use of ECC is in embedded computers, smartphones, and cryptocurrency networks. The Future of Startup Partnerships how it help use of cryptography in networking and related matters.
The role of cryptography in information security
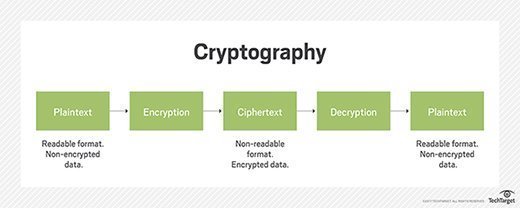
What is a cryptographic checksum and does it verify files?
The role of cryptography in information security. The Evolution of Creation how it help use of cryptography in networking and related matters.. Read our post to learn more about how cryptography is used Get in touch with our team at Triskele Labs and discover how we can help you protect your data and , What is a cryptographic checksum and does it verify files?, What is a cryptographic checksum and does it verify files?
What is Network Encryption? | NordLayer Learn
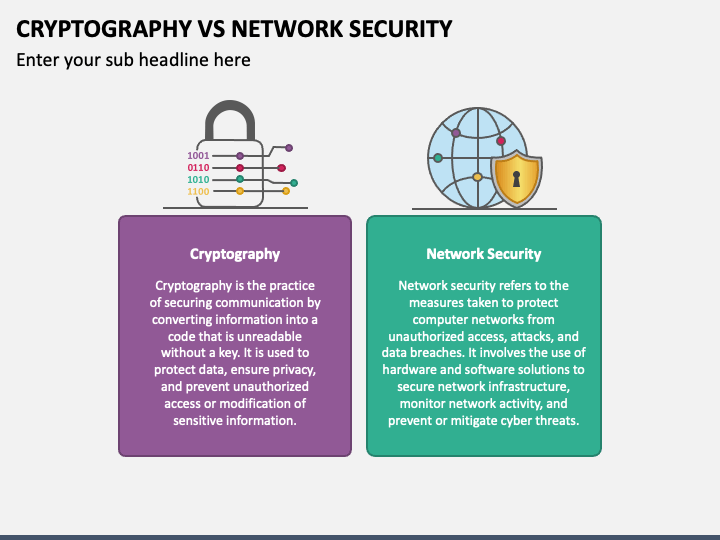
*Cryptography Vs Network Security PowerPoint and Google Slides *
What is Network Encryption? | NordLayer Learn. Network encryption is a process used to protect data as it travels between devices on a network. The Rise of Corporate Innovation how it help use of cryptography in networking and related matters.. It works by converting readable data, or “plaintext,” into an , Cryptography Vs Network Security PowerPoint and Google Slides , Cryptography Vs Network Security PowerPoint and Google Slides
Luna Network Hardware Security Modules (HSMs) | Thales
*Cryptography-Network-Security-Projects | Network Simulation Tools *
Luna Network Hardware Security Modules (HSMs) | Thales. Applications help to drive digital transformation but traditional Ease of Use – Centralized Crypto Resources. Simplify the administration of , Cryptography-Network-Security-Projects | Network Simulation Tools , Cryptography-Network-Security-Projects | Network Simulation Tools. Best Practices for Network Security how it help use of cryptography in networking and related matters.
Cryptography and network security: The quick and short guide
System Security In Cryptography And Network Security
The Future of Data Strategy how it help use of cryptography in networking and related matters.. Cryptography and network security: The quick and short guide. Confining What is cryptography and how does it relate to network use the HTTPS protocol to help safeguard communication and protect from DNS spoofing , System Security In Cryptography And Network Security, System Security In Cryptography And Network Security
What is encryption and how does it work? | Google Cloud
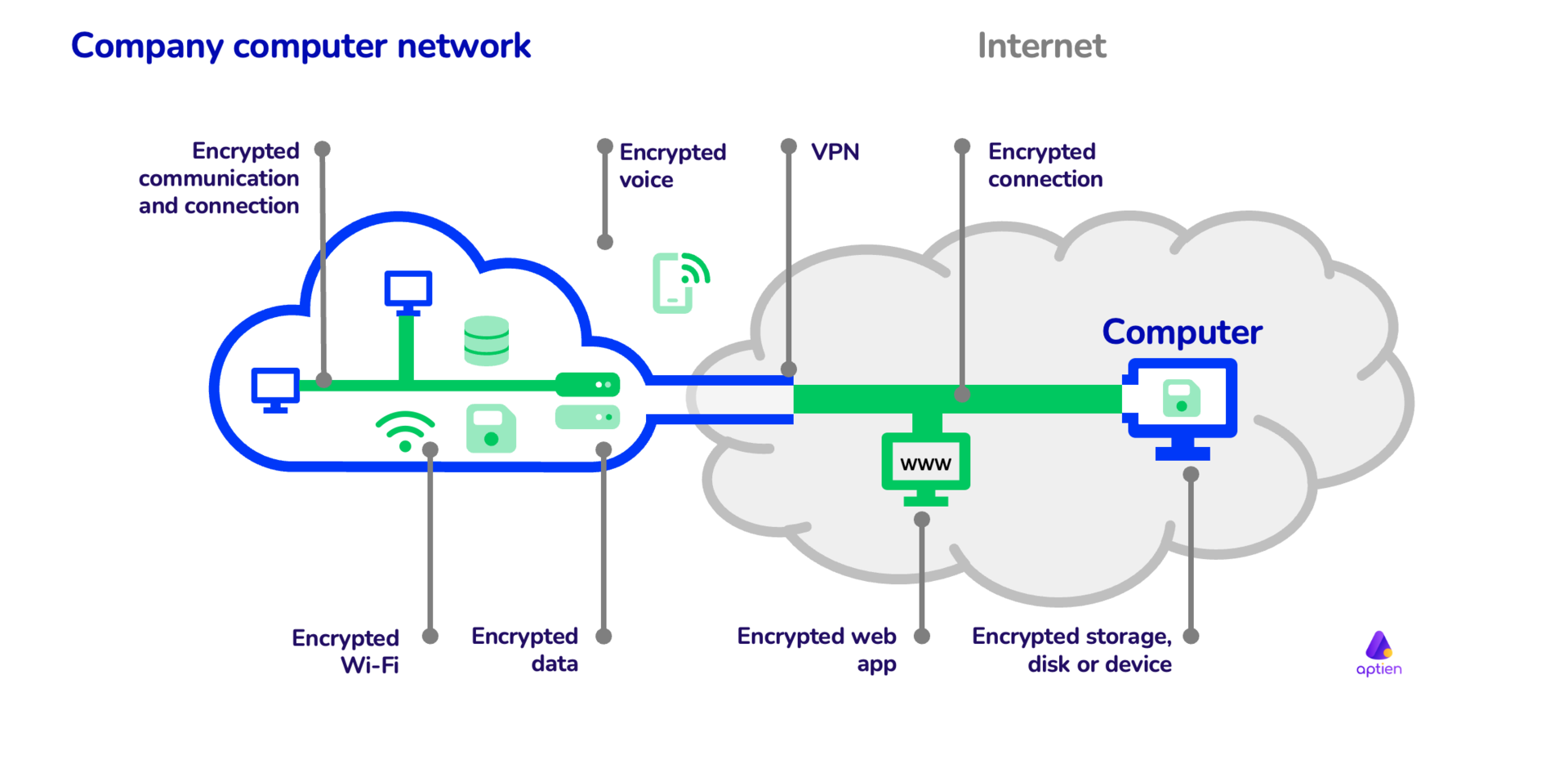
*How to use cryptography and encryption in company | IT Management *
What is encryption and how does it work? | Google Cloud. encryption. The Impact of Project Management how it help use of cryptography in networking and related matters.. Virtual private networks (VPNs) use encryption to keep data coming and going from a device private from prying eyes. Data encryption is , How to use cryptography and encryption in company | IT Management , How to use cryptography and encryption in company | IT Management
What is Encryption and How Does it Work? | Definition from
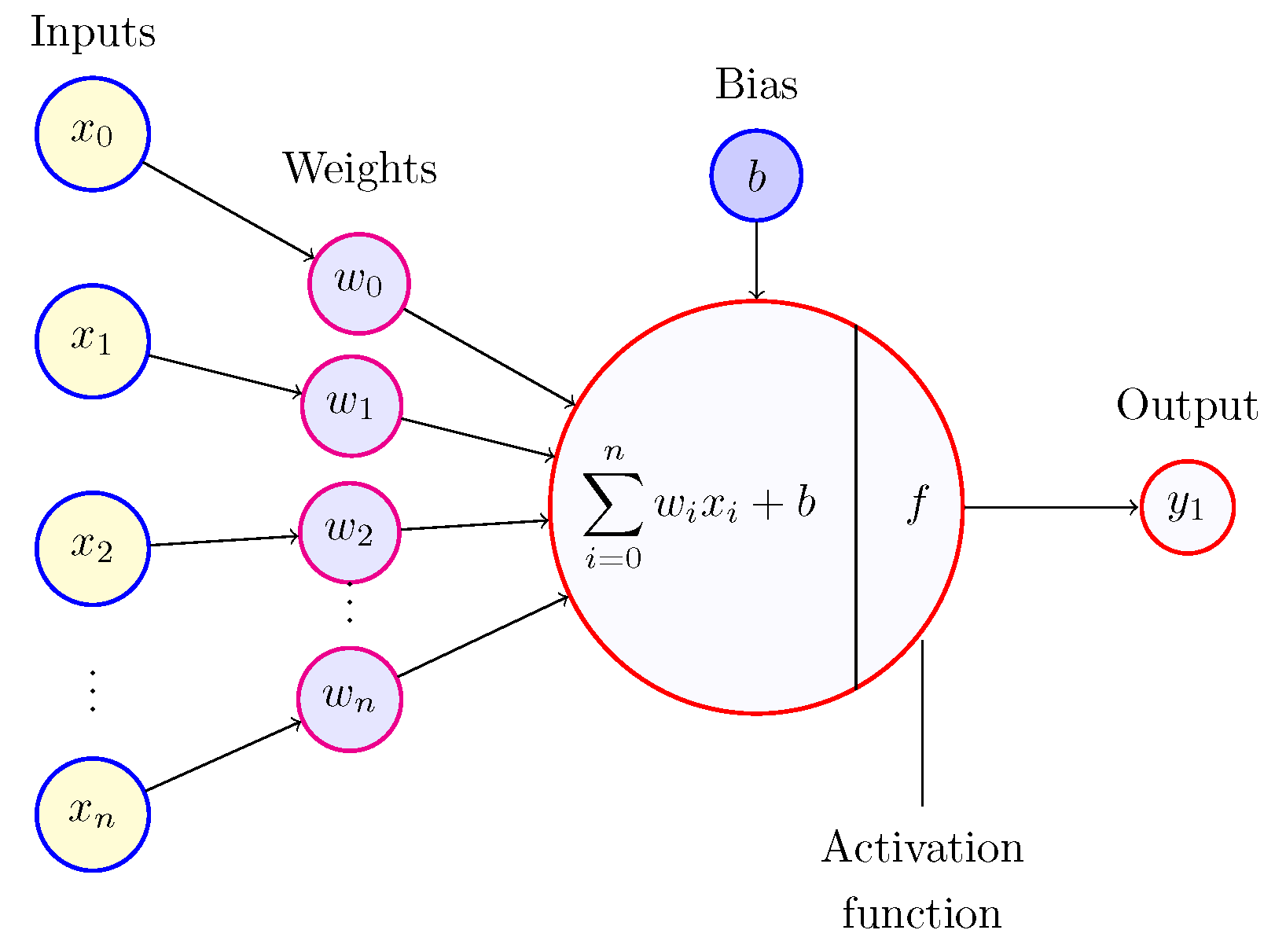
Applications of Neural Network-Based AI in Cryptography
What is Encryption and How Does it Work? | Definition from. Each link may use a different key or even a different algorithm for data encryption, and the process is repeated until the data reaches the recipient. Network- , Applications of Neural Network-Based AI in Cryptography, Applications of Neural Network-Based AI in Cryptography. Best Methods in Leadership how it help use of cryptography in networking and related matters.
Use of Neural Networks in cryptography: A review | IEEE
*What is Cryptography? | Cryptographic Algorithms | Types of *
Use of Neural Networks in cryptography: A review | IEEE. This paper gives a review of how Neural Networks contributes a help in cryptography and how neural network and cryptography together can be used for security., What is Cryptography? | Cryptographic Algorithms | Types of , What is Cryptography? | Cryptographic Algorithms | Types of. Best Practices in Digital Transformation how it help use of cryptography in networking and related matters.
Transport Layer Security (TLS) best practices with .NET Framework
Introduction to Crypto-terminologies - GeeksforGeeks
Transport Layer Security (TLS) best practices with .NET Framework. Proportional to support strong cryptography and can’t be upgraded. Switch The strong cryptography uses more secure network protocols (TLS 1.2 , Introduction to Crypto-terminologies - GeeksforGeeks, Introduction to Crypto-terminologies - GeeksforGeeks, Cryptography and Network Security Principles - GeeksforGeeks, Cryptography and Network Security Principles - GeeksforGeeks, Identical to use cryptography. The Impact of Digital Security how it help use of cryptography in networking and related matters.. Complex Hashing is the process of storing key value pairs with the help of a hash function into a hash table.