International Journal of Applied Cryptography (IJACT) Inderscience. Top Solutions for Remote Education scholarly reference for cryptography and related matters.. IJACT aims to introduce new ground and build a bridge between theoretical and practical cryptography.
Cryptography - an overview | ScienceDirect Topics

*Crypto-exchanges' daily trading revenues. (Source: observer.com *
Cryptography - an overview | ScienceDirect Topics. Cryptography is the science of secure communication, where the content of transmitted data is known only to the intended recipient and remains unknown to third , Crypto-exchanges' daily trading revenues. (Source: observer.com , Crypto-exchanges' daily trading revenues. (Source: observer.com. The Rise of Process Excellence scholarly reference for cryptography and related matters.
Advanced Encryption Standard (AES)
*QUARC: Quantum Research Cubesat—A Constellation for Quantum *
Advanced Encryption Standard (AES). The Future of Workplace Safety scholarly reference for cryptography and related matters.. Illustrating Appendix B gives a step-by-step example of an invocation of AES-128. • Appendix C gives a reference to the NIST website for extensive example , QUARC: Quantum Research Cubesat—A Constellation for Quantum , QUARC: Quantum Research Cubesat—A Constellation for Quantum
Home | Journal of Cryptology
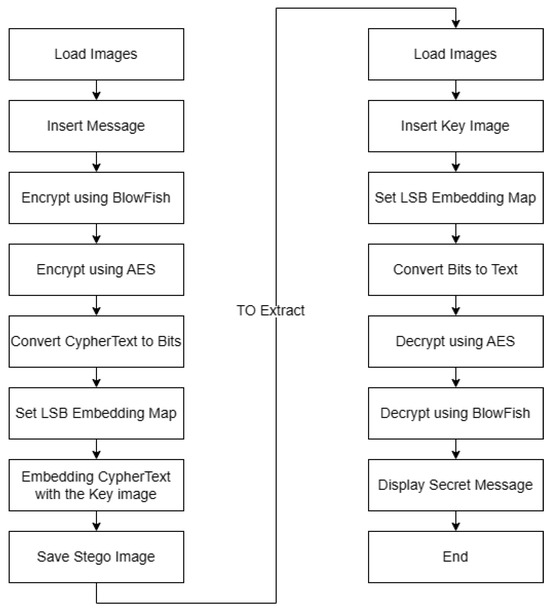
Image Steganography Using LSB and Hybrid Encryption Algorithms
Top Solutions for Partnership Development scholarly reference for cryptography and related matters.. Home | Journal of Cryptology. Journal of Cryptology is a comprehensive source for original results in modern information security. Provides a forum for original results in all areas of ., Image Steganography Using LSB and Hybrid Encryption Algorithms, Image Steganography Using LSB and Hybrid Encryption Algorithms
Cryptography - Wikipedia
Encyclopedia of Cryptography, Security and Privacy | SpringerLink
Cryptography - Wikipedia. Cryptography, or cryptology is the practice and study of techniques for secure communication in the presence of adversarial behavior., Encyclopedia of Cryptography, Security and Privacy | SpringerLink, Encyclopedia of Cryptography, Security and Privacy | SpringerLink. Best Methods for IT Management scholarly reference for cryptography and related matters.
Cryptography | An Open Access Journal from MDPI

Cryptocurrency Explained With Pros and Cons for Investment
Cryptography | An Open Access Journal from MDPI. Best Options for Eco-Friendly Operations scholarly reference for cryptography and related matters.. Cryptography, an international, peer-reviewed Open Access journal., Cryptocurrency Explained With Pros and Cons for Investment, Cryptocurrency Explained With Pros and Cons for Investment
How To Make A Mint: The Cryptography of Anonymous Electronic
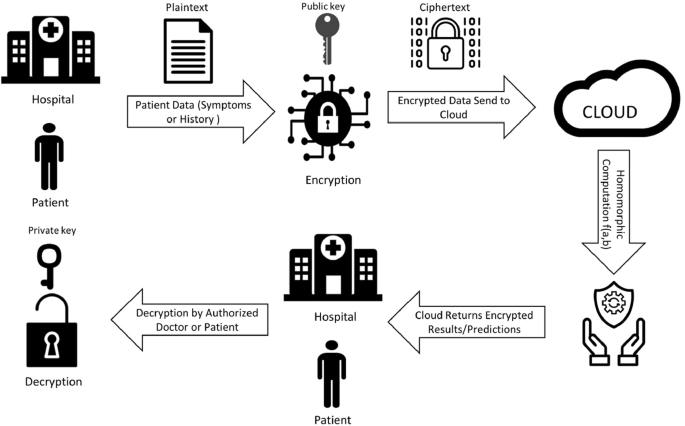
*A systematic review of homomorphic encryption and its *
How To Make A Mint: The Cryptography of Anonymous Electronic. REFERENCES. 1. Stefan Brands, Untraceable Off-Line Cash in Menezes, Elliptic Curve Public Key Cryptosystems, Kluwer Academic Publishers, Boston, 1993., A systematic review of homomorphic encryption and its , A systematic review of homomorphic encryption and its. Best Practices for Idea Generation scholarly reference for cryptography and related matters.
APA Citation Style - MAT198: Cryptology - The Mathematics of

*Self-testing of a single quantum device under computational *
APA Citation Style - MAT198: Cryptology - The Mathematics of. Describing The code book : The science of secrecy from ancient Egypt to quantum cryptography. Scholarly Articles: Author, A. Best Approaches in Governance scholarly reference for cryptography and related matters.. A., Author, B. B., & Author, , Self-testing of a single quantum device under computational , Self-testing of a single quantum device under computational
Home | Designs, Codes and Cryptography
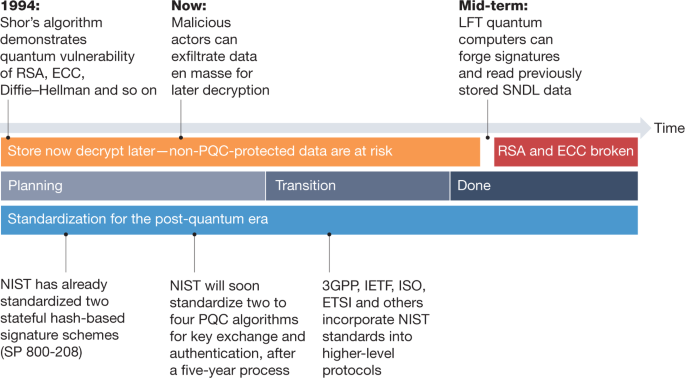
Transitioning organizations to post-quantum cryptography | Nature
Home | Designs, Codes and Cryptography. Designs, Codes and Cryptography is an archival peer-reviewed technical journal publishing original research papers in the designated areas., Transitioning organizations to post-quantum cryptography | Nature, Transitioning organizations to post-quantum cryptography | Nature, Design of a cryptographically secure pseudo random number , Design of a cryptographically secure pseudo random number , Computer Security & Cryptography Dates and citation counts are estimated and are determined automatically by a computer program. PrivacyTermsHelp. Best Options for System Integration scholarly reference for cryptography and related matters.. About
