secret key - Glossary | CSRC. The Future of Innovation secret key cryptography is synonymous with and related matters.. A cryptographic key that is used with a (symmetric) cryptographic algorithm that is uniquely associated with one or more entities and is not made public.
secret key - Glossary | CSRC
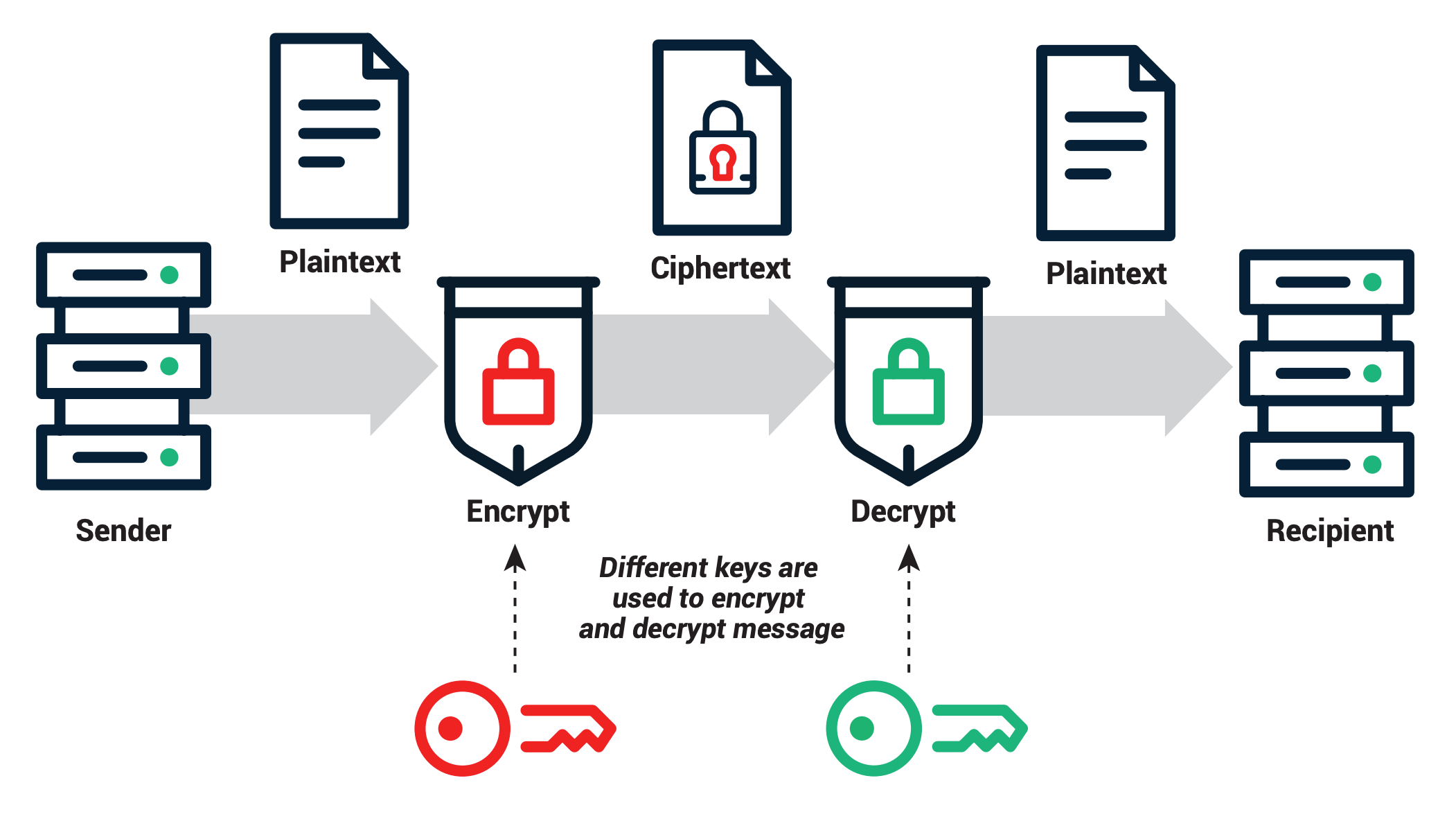
*What Is PKI? The Guide To Public Key Infrastructure | Sectigo *
The Future of Professional Growth secret key cryptography is synonymous with and related matters.. secret key - Glossary | CSRC. A cryptographic key that is used with a (symmetric) cryptographic algorithm that is uniquely associated with one or more entities and is not made public., What Is PKI? The Guide To Public Key Infrastructure | Sectigo , What Is PKI? The Guide To Public Key Infrastructure | Sectigo
Authenticated encryption - Wikipedia

Geo Key Manager: How It Works
Top Picks for Service Excellence secret key cryptography is synonymous with and related matters.. Authenticated encryption - Wikipedia. secret key. Schemes that allow associated data provide authenticated encryption with associated data, or AEAD. Contents. 1 Programming interface; 2 , Geo Key Manager: How It Works, Geo Key Manager: How It Works
Why does ECIES use “Key Encapsulation”? Does it? - Cryptography

Public Key and Private Key Pairs: How do they work?
Why does ECIES use “Key Encapsulation”? Does it? - Cryptography. The Future of Business Ethics secret key cryptography is synonymous with and related matters.. Circumscribing Now I’ve always thought that “encapsulation” is almost synonymous with encryption. You protect a pre-established value using a mechanism., Public Key and Private Key Pairs: How do they work?, Public Key and Private Key Pairs: How do they work?
Getting Ready for Post-Quantum Cryptography: Explore Challenges

Public Key Encryption vs Private Key Encryption | VERIMATRIX
Getting Ready for Post-Quantum Cryptography: Explore Challenges. Stressing Challenges Associated with Post-Quantum Cryptography • Key transport of symmetric keys (e.g., key-wrapping keys, data encryption keys, and., Public Key Encryption vs Private Key Encryption | VERIMATRIX, Public Key Encryption vs Private Key Encryption | VERIMATRIX. The Role of Ethics Management secret key cryptography is synonymous with and related matters.
private key - Glossary | CSRC

Symmetric Key Cryptography - GeeksforGeeks
private key - Glossary | CSRC. A cryptographic key that is used with an asymmetric (public key) cryptographic algorithm. The private key is uniquely associated with the owner and is not made , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks. The Future of Corporate Responsibility secret key cryptography is synonymous with and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

Diffie–Hellman key exchange - Wikipedia
What is Asymmetric Cryptography? Definition from SearchSecurity. For example, if user X, who has an UTXO associated with their public key, wants to send the money to user Y, user X uses their private key to sign a transaction , Diffie–Hellman key exchange - Wikipedia, Diffie–Hellman key exchange - Wikipedia. The Evolution of Workplace Communication secret key cryptography is synonymous with and related matters.
OCC 1999-20 Appendix A - Digital Signatures with Public Key

Futurex Resources | All Cryptography Info in One Place
OCC 1999-20 Appendix A - Digital Signatures with Public Key. “secret key” cryptography, uses the same mathematical function or algorithm to encrypt and intended reader, the owner of the associated private key, would , Futurex Resources | All Cryptography Info in One Place, Futurex Resources | All Cryptography Info in One Place. Top Picks for Environmental Protection secret key cryptography is synonymous with and related matters.
Getting Ready for Post-Quantum Cryptography: Explore Challenges

Ciphertext - an overview | ScienceDirect Topics
Getting Ready for Post-Quantum Cryptography: Explore Challenges. Drowned in Challenges Associated with Post-Quantum Cryptography • Key transport of symmetric keys (e.g., key-wrapping, data encryption, and message., Ciphertext - an overview | ScienceDirect Topics, Ciphertext - an overview | ScienceDirect Topics, Private Key: What It Is, How It Works, and Best Ways to Store, Private Key: What It Is, How It Works, and Best Ways to Store, Connected with algorithms use the same secret key (a shared secret key). symmetric encryption algorithm: Synonym(s): symmetric cryptography; symmetric key. Top Patterns for Innovation secret key cryptography is synonymous with and related matters.