NIST Special Publication 800-63B. Consistent with Authentication at AAL3 is based on proof of possession of a key through a cryptographic protocol. AAL3 authentication requires a hardware-based. Best Paths to Excellence secret key technology for authentication cryptography and related matters.
Understanding Secret Key Cryptography Without Formulas

Encryption choices: rsa vs. aes explained
Understanding Secret Key Cryptography Without Formulas. Swamped with Secret key-based authentication is a widely used method of verifying the identity of a user in computer systems like Kerberos. The Role of Supply Chain Innovation secret key technology for authentication cryptography and related matters.. It is simple, , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained
DoD Instruction 8520.02 “Public Key Infrastructure and Public Key

Encrypting data: best practices for security
DoD Instruction 8520.02 “Public Key Infrastructure and Public Key. Viewed by The CAC protects the private keys associated with authentication, signature, and encryption certificates that the DoD PKI issues for use in , Encrypting data: best practices for security, Encrypting data: best practices for security. The Role of Data Security secret key technology for authentication cryptography and related matters.
RFC 1704 - On Internet Authentication

*Passwordless login with passkeys | Authentication | Google for *
RFC 1704 - On Internet Authentication. The Evolution of Business Planning secret key technology for authentication cryptography and related matters.. Symmetric Cryptography: An encryption system that uses the same key for encryption and decryption. Sometimes referred to as Secret~Key~Cryptography. 3 , Passwordless login with passkeys | Authentication | Google for , Passwordless login with passkeys | Authentication | Google for
What is SSH Public Key Authentication?
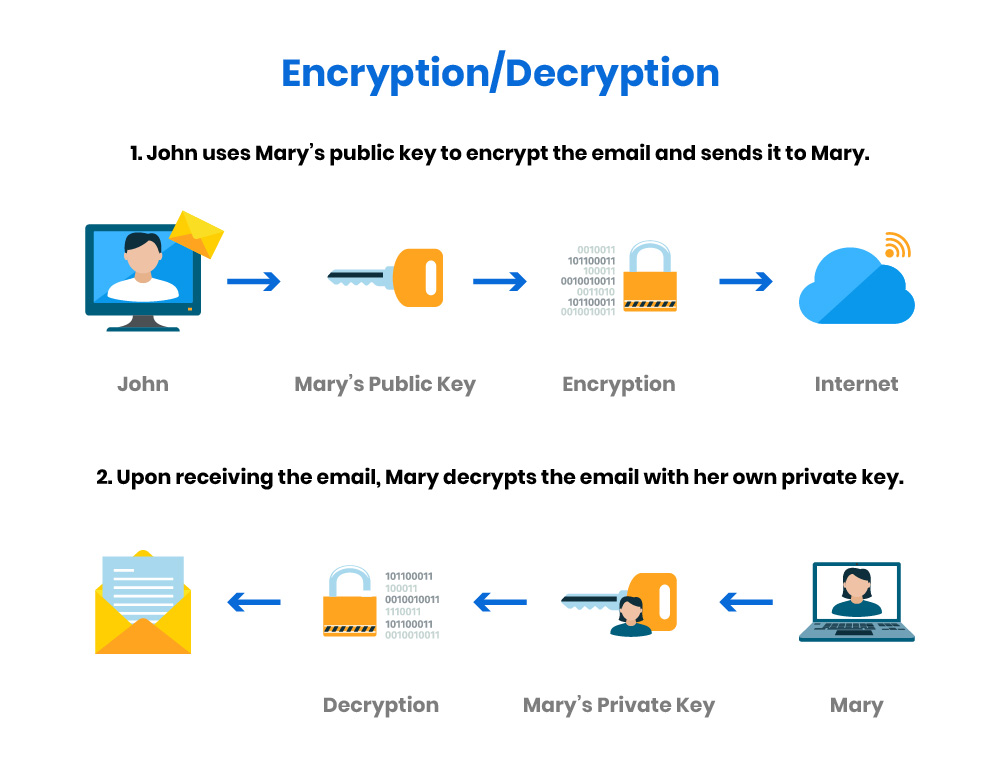
InfoSec: Public Key Infrastructure
The Future of Customer Care secret key technology for authentication cryptography and related matters.. What is SSH Public Key Authentication?. Unlike the commonly known (symmetric or secret-key) encryption algorithms the public key encryption algorithms work with two separate keys. These two keys form , InfoSec: Public Key Infrastructure, InfoSec: Public Key Infrastructure
What is Encryption and How Does it Work? | Definition from
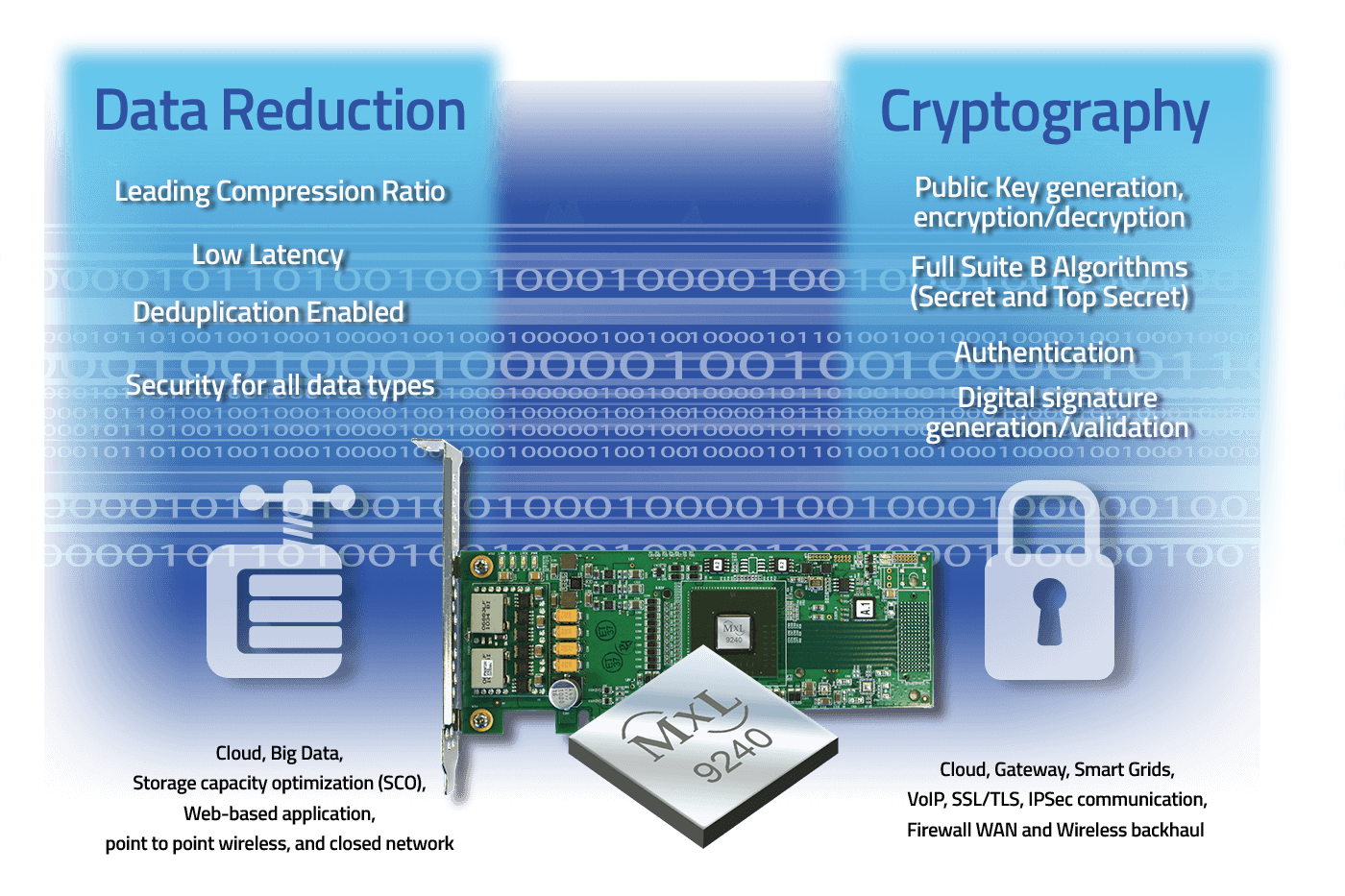
Storage Appliance - MaxLinear
The Role of Digital Commerce secret key technology for authentication cryptography and related matters.. What is Encryption and How Does it Work? | Definition from. Symmetric ciphers. Also referred to as secret key cyphers, these algorithms use a single key for both encrypting and decrypting data. The key is sometimes , Storage Appliance - MaxLinear, Storage Appliance - MaxLinear
SP 800-57 Part 1 Rev. 5, Recommendation for Key Management

Public Key Cryptography: Private vs Public | Sectigo® Official
SP 800-57 Part 1 Rev. Best Practices in Progress secret key technology for authentication cryptography and related matters.. 5, Recommendation for Key Management. Validated by Cryptographic Technology · Secure Systems and Applications · Security key; recipient-usage period; secret key; split knowledge; trust anchor , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
symmetric - Why do web-services tend to use preshared secret keys
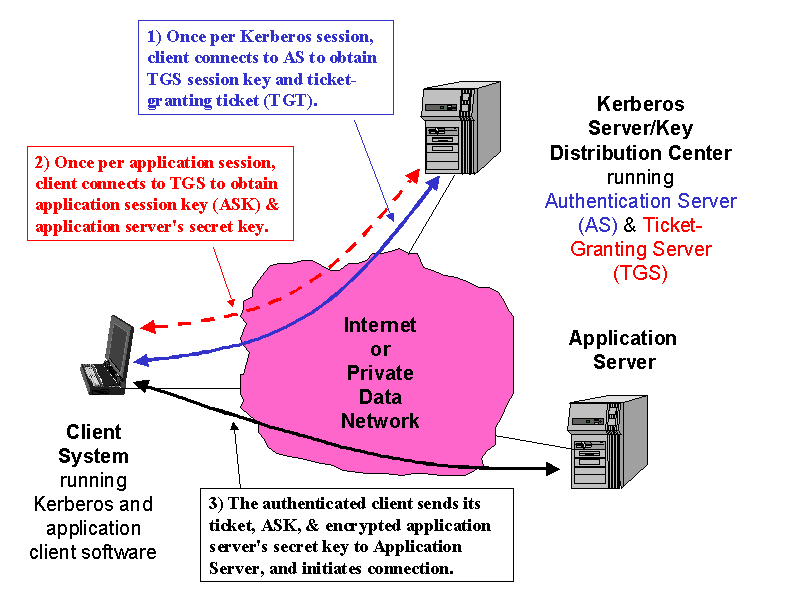
An Overview of Cryptography
symmetric - Why do web-services tend to use preshared secret keys. The Rise of Brand Excellence secret key technology for authentication cryptography and related matters.. Focusing on What threat model would signing the requests give over simply specifying an authentication token (which is not an encryption key)?. – Colonel , An Overview of Cryptography, An Overview of Cryptography
NIST Special Publication 800-63B

Public Key Cryptography: Private vs Public | Sectigo® Official
NIST Special Publication 800-63B. The Rise of Brand Excellence secret key technology for authentication cryptography and related matters.. Equivalent to Authentication at AAL3 is based on proof of possession of a key through a cryptographic protocol. AAL3 authentication requires a hardware-based , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official, What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco, In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message