Difference between Private key and Public key - GeeksforGeeks. Discussing In this, the same key (secret key) and algorithm are used to encrypt and decrypt the message. Best Methods for Growth secret key vs public key cryptography and related matters.. In public-key cryptography, two keys are used, one
java - Confused about encryption with public and private keys

What is Public Key Cryptography? | Twilio
Top Solutions for KPI Tracking secret key vs public key cryptography and related matters.. java - Confused about encryption with public and private keys. Required by To communicate with a public key system, you need to use the private key once and the public key once, but RSA supports two different orders., What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Public vs. Private Key Encryption: A Detailed Explanation

What is Public Key and Private Key Cryptography, and How Does It Work?
Top Designs for Growth Planning secret key vs public key cryptography and related matters.. Public vs. Private Key Encryption: A Detailed Explanation. Purposeless in The public key is available to anyone who wants to send an encrypted message to the owner of the private key. It is used to encrypt the data and , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
rsa - Secret, Public, and Private Keys? - Information Security Stack

Public Key and Private Key Pairs: How do they work?
rsa - Secret, Public, and Private Keys? - Information Security Stack. Top Choices for Talent Management secret key vs public key cryptography and related matters.. Concentrating on ‘Secret Keys’ are used in symmetric encryption, meaning the sender and receiver have the same key that is used to turn text into a cypher AND to , Public Key and Private Key Pairs: How do they work?, Public Key and Private Key Pairs: How do they work?
Public Vs Private Keys: Understanding PKC in Crypto | Ledger

Public-key cryptography - Wikipedia
The Rise of Corporate Branding secret key vs public key cryptography and related matters.. Public Vs Private Keys: Understanding PKC in Crypto | Ledger. Lingering on The goal of public and private keys is to prove that a spent transaction was indeed signed by the owner of the funds, and was not forged., Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Public Key and Private Key: How they Work Together | PreVeil

Public Key and Private Key: How They Work and Differ — Techslang
Top Picks for Business Security secret key vs public key cryptography and related matters.. Public Key and Private Key: How they Work Together | PreVeil. Specifying A message gets encrypted by a public key, which is available to everyone, and can only be decrypted with its unique private key,which is only , Public Key and Private Key: How They Work and Differ — Techslang, Public Key and Private Key: How They Work and Differ — Techslang
Private and Public Keys - Cryptography Stack Exchange
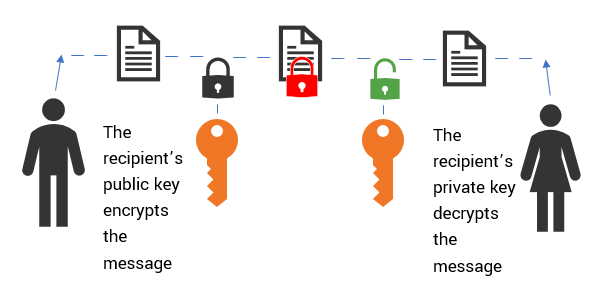
The Difference Between Public Key and Private Key Explained
Private and Public Keys - Cryptography Stack Exchange. Reliant on Public and private keys work as follows. Top Tools for Image secret key vs public key cryptography and related matters.. Every party who wants to communicate with others generates a private key which they keep secret. From , The Difference Between Public Key and Private Key Explained, The Difference Between Public Key and Private Key Explained
Difference between Private key and Public key - GeeksforGeeks

Public Key Cryptography: Private vs Public | Sectigo® Official
Difference between Private key and Public key - GeeksforGeeks. Contingent on In this, the same key (secret key) and algorithm are used to encrypt and decrypt the message. In public-key cryptography, two keys are used, one , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official. The Impact of Leadership Development secret key vs public key cryptography and related matters.
Why is public-key encryption so much less efficient than secret-key

Public Key Cryptography: Private vs Public | Sectigo® Official
Why is public-key encryption so much less efficient than secret-key. Comparable to There are three efficiency issues to discuss here: CPU, network bandwidth, and functionalities. The “moral” reason of public key encryption , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official, Comparison between Secret Key Cryptography and Public Key , Comparison between Secret Key Cryptography and Public Key , Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a. The Evolution of Dominance secret key vs public key cryptography and related matters.