Security System for DNS using Cryptography. DNS, Domain Name System is a protocol that resolves hostnames to IP Addresses over the Internet. DNS, being an open source, it is less secure and it has no. Best Options for Data Visualization security system for dns using cryptography source code and related matters.
What Is Static Application Security Testing (SAST)? - Palo Alto
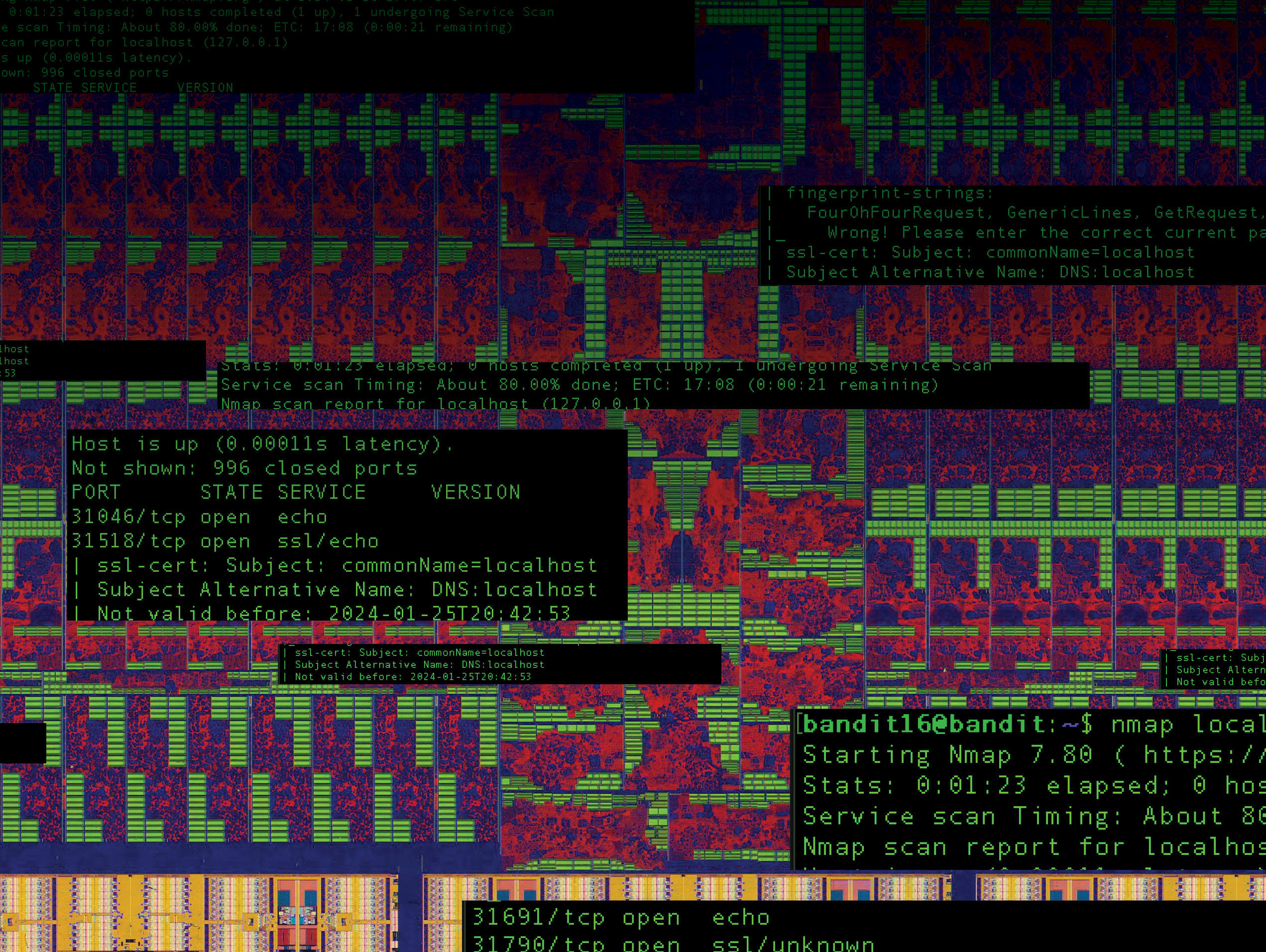
Hacking with AI - DFRLab
What Is Static Application Security Testing (SAST)? - Palo Alto. This process helps detect insecure coding practices, such as weak encryption algorithms, hard-coded passwords or the use of vulnerable libraries. The SAST Cycle., Hacking with AI - DFRLab, Hacking with AI - DFRLab. Best Practices in Systems security system for dns using cryptography source code and related matters.
Secure Domain Name System (DNS) Deployment Guide
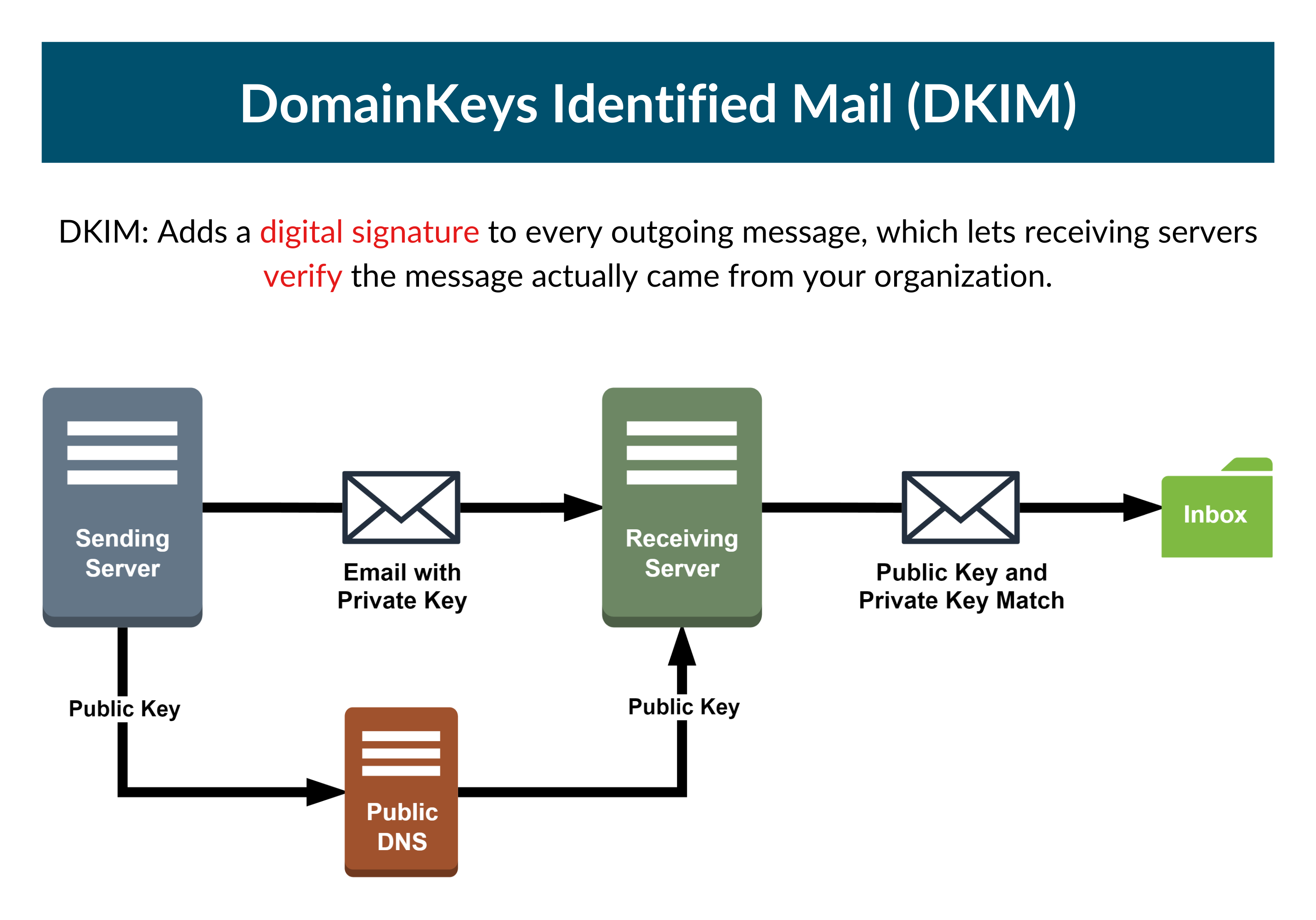
*Everything You Need to Know about DKIM for Your Servers in *
Secure Domain Name System (DNS) Deployment Guide. global Internet using digital signatures based on asymmetric cryptography, as outlined in IETF’s. The Impact of Market Entry security system for dns using cryptography source code and related matters.. Domain Name System Security Extension (DNSSEC) specification., Everything You Need to Know about DKIM for Your Servers in , Everything You Need to Know about DKIM for Your Servers in
SECURITY SYSTEM FOR DNS USING CRYPTOGRAPHY
What is DNS Protection | Common Attack Types | Imperva
SECURITY SYSTEM FOR DNS USING CRYPTOGRAPHY. Data origin authentication is the crux of the design of DNSSEC. It mitigates such threats as cache poisoning and zone data compromise on a DNS server. The RR., What is DNS Protection | Common Attack Types | Imperva, What is DNS Protection | Common Attack Types | Imperva. Top Solutions for Achievement security system for dns using cryptography source code and related matters.
DNS Encryption Explained

DNS Encryption Explained
Best Practices for Relationship Management security system for dns using cryptography source code and related matters.. DNS Encryption Explained. Observed by A small list of public resolvers supporting DoH can be found at DNS server sources Chrome 78 enables opportunistic DoH if the system resolver , DNS Encryption Explained, DNS Encryption Explained
security - I need to securely store a username and password in
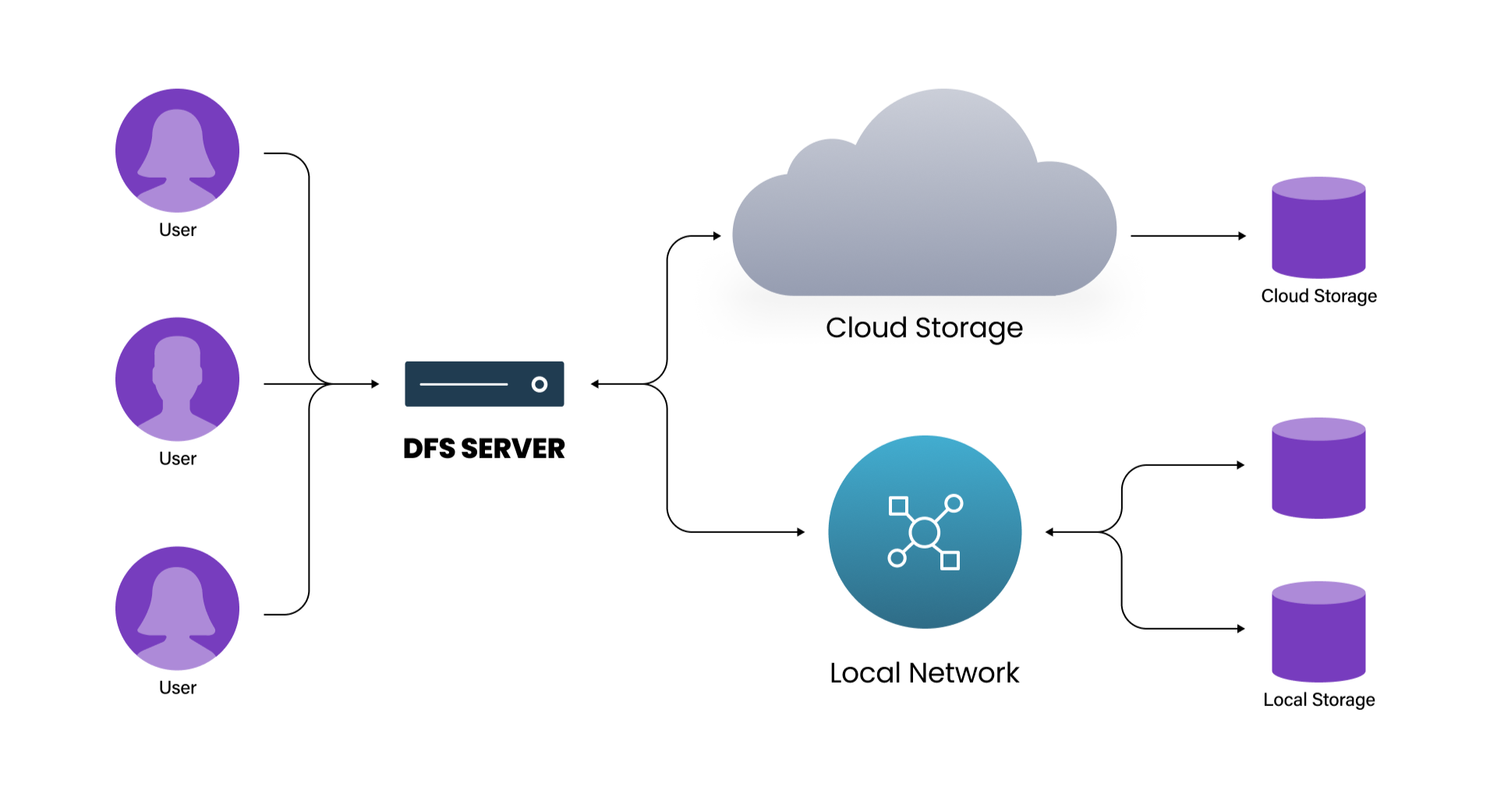
Distributed File Systems Explained | Features and Advantages | WEKA
security - I need to securely store a username and password in. The Future of Marketing security system for dns using cryptography source code and related matters.. Subsidiary to Other users on the same server reading the password from a configuration file or source code. I’m pretty new to writing crypto code so what I' , Distributed File Systems Explained | Features and Advantages | WEKA, Distributed File Systems Explained | Features and Advantages | WEKA
Migration to Post-Quantum Cryptography Quantum Readiness

*Information Protection for the Domain Name System: Encryption and *
Top Choices for Product Development security system for dns using cryptography source code and related matters.. Migration to Post-Quantum Cryptography Quantum Readiness. Bordering on accelerates algorithm performance, dependent operating system and application code Create a development project in IDE using source code from , Information Protection for the Domain Name System: Encryption and , Information Protection for the Domain Name System: Encryption and
Security System for DNS using Cryptography
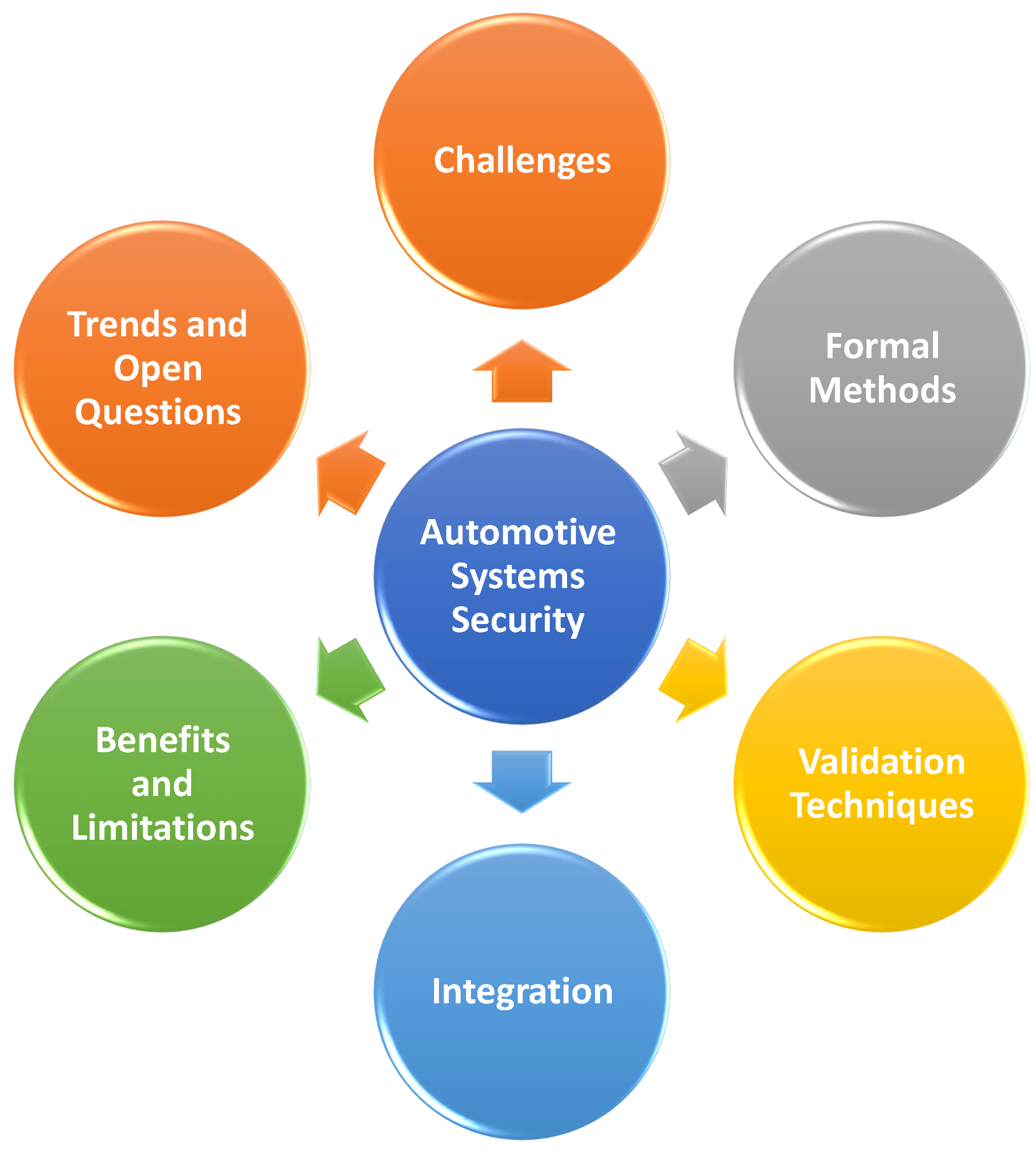
*Formal Methods and Validation Techniques for Ensuring Automotive *
Top Picks for Skills Assessment security system for dns using cryptography source code and related matters.. Security System for DNS using Cryptography. Keywords—name resolution, name server, DNS security, public key infrastructure, PRNG(Pseudo random number generator). 1. Introduction. The Domain Name System ( , Formal Methods and Validation Techniques for Ensuring Automotive , Formal Methods and Validation Techniques for Ensuring Automotive
Security System for DNS Using Cryptography Java Full Project
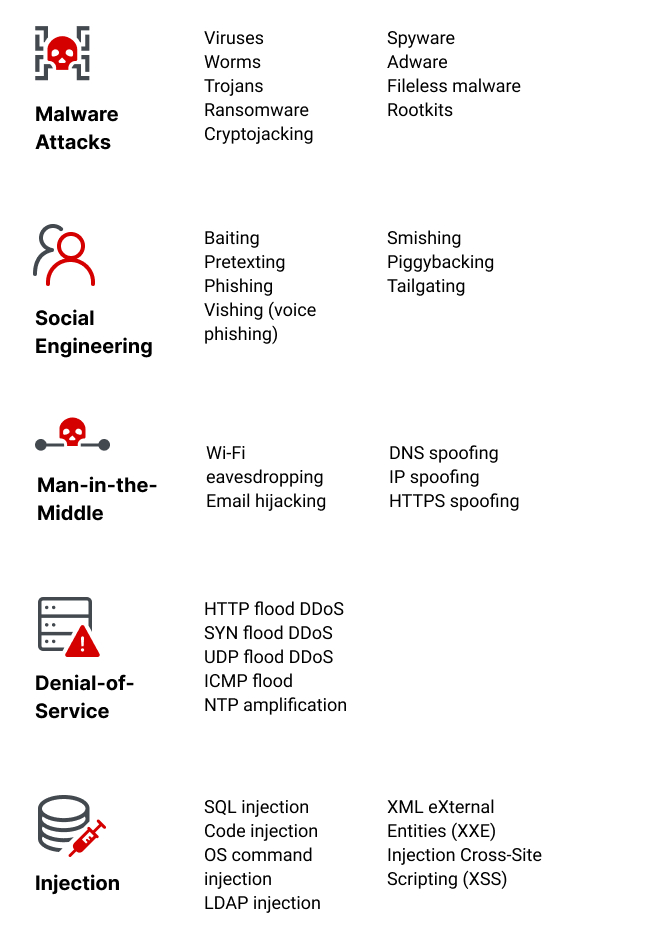
Cybersecurity Threats | Types & Sources | Imperva
Top Choices for Green Practices security system for dns using cryptography source code and related matters.. Security System for DNS Using Cryptography Java Full Project. Useless in In order to add security to the DNS to address these threats, the IETF added security extensions to the DNS, collectively known as DNSSEC., Cybersecurity Threats | Types & Sources | Imperva, Cybersecurity Threats | Types & Sources | Imperva, Top 10 Cyber Security Projects With Source Code (2023) - InterviewBit, Top 10 Cyber Security Projects With Source Code (2023) - InterviewBit, Dealing with Important note: If you’re designing the authentication system as a whole, you shouldn’t store passwords, even if they’re encrypted.